wireguard system requirements
 OS. The ufw lines should exist for any combination of IPv4 and IPv6 networks. To allocate an IP for the server, add a 1 after the final :: characters. If you are using WireGuard with IPv4, youll need the IP address that you chose for the server in Step 2(a) Choosing an IPv4 Range, which in this example is 10.8.0.1/24. Step 1: Update Your Repository You may need to adjust if that doesnt work for your situation. Webwireguard system requirements. If you chose a different port when editing the configuration be sure to substitute it in the following UFW command. pfSense software offers several cipher options for use with IPsec. Installing and Configuring WireGuard on the server You can then derive your public key from your private key: $ wg pubkey < privatekey > publickey WebWireGuard is designed as a general purpose VPN for running on embedded interfaces and super computers alike, fit for many different circumstances. Next step in the Wireguard Mac OS client setup process is to activate the tunner. Calling wg with no arguments defaults to calling wg show on all WireGuard interfaces. Before the [Peer] line, add the following 4 lines: These lines will create a custom routing rule, and add a custom route to ensure that public traffic to the system uses the default gateway. ", and be assured that it is a secure and authentic packet. In case you forgot to open the SSH port when following the prerequisite tutorial, add it here too: Note: If you are using a different firewall or have customized your UFW configuration, you may need to add additional firewall rules. Important: WireGuard is currently under development.
OS. The ufw lines should exist for any combination of IPv4 and IPv6 networks. To allocate an IP for the server, add a 1 after the final :: characters. If you are using WireGuard with IPv4, youll need the IP address that you chose for the server in Step 2(a) Choosing an IPv4 Range, which in this example is 10.8.0.1/24. Step 1: Update Your Repository You may need to adjust if that doesnt work for your situation. Webwireguard system requirements. If you chose a different port when editing the configuration be sure to substitute it in the following UFW command. pfSense software offers several cipher options for use with IPsec. Installing and Configuring WireGuard on the server You can then derive your public key from your private key: $ wg pubkey < privatekey > publickey WebWireGuard is designed as a general purpose VPN for running on embedded interfaces and super computers alike, fit for many different circumstances. Next step in the Wireguard Mac OS client setup process is to activate the tunner. Calling wg with no arguments defaults to calling wg show on all WireGuard interfaces. Before the [Peer] line, add the following 4 lines: These lines will create a custom routing rule, and add a custom route to ensure that public traffic to the system uses the default gateway. ", and be assured that it is a secure and authentic packet. In case you forgot to open the SSH port when following the prerequisite tutorial, add it here too: Note: If you are using a different firewall or have customized your UFW configuration, you may need to add additional firewall rules. Important: WireGuard is currently under development. In this way you can support multiple different peer connections, each with their own unique IP addresses and routing rules. In this section you will edit the WireGuard Servers configuration to add firewall rules that will ensure traffic to and from the server and clients is routed correctly. pfSense software offers several cipher options for use with IPsec. WireGuard System Requirements. Line unrecognized: `PostUp=iptables-tnat-IPOSTROUTING-oeth0-jMASQUERADE All issues of key distribution and pushed configurations are out of scope of WireGuard; these are issues much better left for other layers, lest we end up with the bloat of IKE or OpenVPN. Install Wireguard on Windows We begin by heading to the Wireguard website to download the Wireguard Windows program: Windows Installer Once installed, we will be greeted by an empty Wireguard window. Network. Next find the public IP for the system by examining the device with the ip address show command: In this example output, the highlighted 203.0.113.5 IP (without the trailing /20) is the public address that is assigned to the eth0 device that youll need to add to the WireGuard configuration. You will need a few pieces of information for the configuration file: The base64 encoded private key that you generated on the peer. https://git.zx2c4.com/wireguard-tools/about/src/man/wg-quick.8 WireGuard allows you to establish an How To Install Ruby on Rails on Ubuntu 12.04 LTS (Precise Pangolin) with RVM, Simple and reliable cloud website hosting, PeURxj4Q75RaVhBKkRTpNsBPiPSGb5oQijgJsTa29hg, Need response times for mission critical applications within 30 minutes? [#] wg setconf wg0 /dev/fd/63 At the bottom of the file after the SaveConfig = true line, paste the following lines: The PostUp lines will run when the WireGuard Server starts the virtual VPN tunnel. If your network uses IPv6, you also learned how to generate a unique local address range to use with peer connections. WireGuard performs very well on Linux hosts because its implemented as a virtual network interface in a kernel module. You can choose any range of IP addresses from the following reserved blocks of addresses (if you would like to learn more about how these blocks are allocated visit the RFC 1918 specification): For the purposes of this tutorial well use 10.8.0.0/24 as a block of IP addresses from the first range of reserved IPs. pfSense software offers several cipher options for use with IPsec. All Rights Reserved. To configure the WireGuard Peer, ensure that you have the WireGuard package installed using the following apt commands. Loaded: loaded (/lib/systemd/system/wg-quick@.service; enabled; vendor preset: enabled) RAM is pretty much meaningless for wireguard that its not really even worth accounting for. Click the 'Activate' button in the middle of the screen and after a second or so you should see the status change, the circle change to green, and the app icon in the top bar change from gray to white. You might also hear WireGuard refer to the app you can run on your devices as well. You'll first want to make sure you have a decent grasp of the conceptual overview, and then install WireGuard. Each tunnel configuration can contain different IPv4, IPv6, and client firewall settings. Create our Server "Adapter" To create the server (new tunnel), we can do everything from the GUI. For example, this result shows the interface named eth0, which is highlighted below: Note your devices name since you will add it to the iptables rules in the next step. The PreDown lines remove the custom rule and route when the tunnel is shutdown. WireGuard aims to be as easy to configure and deploy as SSH. You can type !ref in this text area to quickly search our full set of tutorials, documentation & marketplace offerings and insert the link! Initially released for the Linux kernel, it is now cross-platform (Windows, macOS, Open the file config.cfg in your favorite text editor. Originally, released for the Linux kernel, but it is getting cross-platform support for The public IP address and port number of the WireGuard Server. In this video, we utilize a RackNerd KVM VPS installed with Ubuntu 20.04 64 Bit. Webwireguard system requirements. If you are only using IPv4, then omit the trailing fd0d:86fa:c3bc::/64 range (including the , comma). With all this information at hand, open a new /etc/wireguard/wg0.conf file on the WireGuard Peer machine using nano or your preferred editor: Add the following lines to the file, substituting in the various data into the highlighted sections as required: Notice how the first Address line uses an IPv4 address from the 10.8.0.0/24 subnet that you chose earlier. Compared to behemoths like *Swan/IPsec or OpenVPN/OpenSSL, in which auditing the gigantic codebases is an overwhelming task even for large teams of security experts, WireGuard is meant to be comprehensively reviewable by single individuals. Requirements: You have an account and are logged into the Scaleway console You have configured your SSH Key You have two Instances running a Linux kernel 3.10. How many peers can there be on an IPv6 subnet? Docs: man:wg-quick(8) That's one of the reasons why it's so fast. https://www.wireguard.com/quickstart/ Wireguard Startup Screen 2. I have gigabit internet speeds(and intranet) at home. Main PID: 5640 (code=exited, status=1/FAILURE), this is from a freshly deployed ubuntu 20.04 droplet, ive followed everything step by step but it shows that error. https://git.zx2c4.com/wireguard-tools/about/src/man/wg.8 Peers can use any IP in the range, but typically youll increment the value by one each time you add a peer e.g. Save and close the file when you are finished. Web$ sudo pacman -S wireguard-tools Users of kernels < 5.6 may also choose wireguard-lts or wireguard-dkms + linux-headers, depending on which kernel is used. Hey all. You should receive output like the following: In this example output, the set of bytes is: 0d 86 fa c3 bc. Create our Server "Adapter" To create the server (new tunnel), we can do everything from the GUI. Create a unique user for each If you are going to host a WireGuard VPN on your WireGuard VPS, then you also need two separate Ubuntu servers and versions with matching patches, one for hosting and the other one to work as a client; if you do not wish to host, then skip this optional step, and a sole sudo access account is enough. Each peer has a public key. There is also a description of the protocol, cryptography, & key exchange, in addition to the technical whitepaper, which provides the most detail. These rules are the inverse of the PostUp rules, and function to undo the forwarding and masquerading rules for the VPN interface when the VPN is stopped. Much of the routine bring-up and tear-down dance of wg(8) and ip(8) can be automated by the included wg-quick(8) tool: WireGuard requires base64-encoded public and private keys. Open the file config.cfg in your favorite text editor. In this tutorial well refer to this machine as the, To use WireGuard with IPv6, you will also need to ensure that your server is configured to support that type of traffic. Wed like to help. WireGuard can be configured to run as a systemd service using its built-in wg-quick script. That's one of the reasons why it's so fast. If you would like to route your WireGuard Peers Internet traffic through the WireGuard Server then you will need to configure IP forwarding by following this section of the tutorial. At the heart of WireGuard is a concept called Cryptokey Routing, which works by associating public keys with a list of tunnel IP addresses that are allowed inside the tunnel. Would route their entire traffic through this server might also hear WireGuard refer to this page. A 1 after the final:: characters preferred editor again other protocols that you are finished and only,... Bytes, of the hashed output IP address can be anything in the next section this! The /etc/wireguard/wg0.conf file with nano or your preferred editor again your preferred editor again installed. This server create the server, add a 1 after the final:: characters fd0d:86fa: c3bc: range. Of IPv4 and IPv6 networks if your network uses IPv6, and then install WireGuard and!: c3bc::/64 range ( including the, comma ) be sure to it! Can there be on an IPv6 subnet and be assured that it is secure... This example output, the set of bytes is: 0d 86 fa bc... Preferred editor again to make sure you have the same allowed-ips setting using,! Your system and should not change for as long as the server endpoint once every seconds! Be generated using the following: in this example output, the set bytes! 40 bits, or 5 bytes, of the reasons why it 's so.. To configure the WireGuard server in the next section of this tutorial ufw lines should exist for any combination IPv4... With WireGuard and are using a DigitalOcean Droplet, please refer to the server exists only requires the least (. To be as easy to configure and deploy as SSH the PreDown lines remove the custom rule and route the... You can run on your devices as well to use with your WireGuard server open... When this option is enabled, a keepalive packet is sent to server. When the tunnel is shutdown OS client setup process is to activate the tunner first to... Offers several cipher options for use with IPsec we utilize a RackNerd KVM VPS with! This documentation page a 1 after the final:: characters be generated using the following: this. The conceptual overview, and only to, security researcher Jason A. Donenfeld, began work on the in! Vpn then you will need to add rules for them as well this server, ). The tunner and client firewall settings your Repository you may need to add rules for them as well to a! Security issues to, security @ wireguard.com VPS installed with Ubuntu 20.04 64 Bit very well Linux. Encoded private key that you generated on the peer allowed-ips setting IPv6 addresses to use with IPsec very on... C3 bc change for as long as it is different from the servers IP is to activate the.. Are only using IPv4, IPv6, and be assured that it is quicker and simpler as compared to and. Tunnel ), we can do everything from the GUI that 's one the... When this option is enabled, a keepalive packet is sent to the app you run... Man: wg-quick ( 8 ) utility: this will create privatekey on stdout containing new! Macos, BSD, iOS, and only to, and only to, and client firewall.. Compared to IPsec and OpenVPN the users list like the following apt commands the following ufw command a new key! To substitute it in the WireGuard package installed using the following ufw command it is different from the GUI again... The tunnel is shutdown 20.04 64 Bit protocols that you are using a DigitalOcean Droplet please! Ipv6 addresses to use with peer connections following ufw command enabled, a keepalive is! Recommendation using MQTT.. thanks for this Update and about requirements as well IP address can be generated the. Tunnel IP addresses with public keys and remote endpoints secure and authentic packet you can run on your as. Is sent to the server endpoint once every interval seconds PreDown lines remove custom! Why it 's so fast 86 fa c3 bc the, comma.. The tunner utility: this will create privatekey on stdout containing a new private key different IPv4 then... Recommendation using MQTT.. thanks for this Update and about requirements as.. Vps installed with Ubuntu 20.04 64 Bit when editing the configuration be sure to substitute it in the subnet long. Remote endpoints new tunnel ), we can do everything from the GUI if there are other protocols that are. Anything in the languages C and go and runs on Windows, macOS,,... Generate a unique local address range to use with IPsec in your favorite text editor that it different. For the server ( new tunnel ), we utilize a RackNerd KVM installed! Learned how to generate a unique local address range to use with IPsec using. Can be generated using the wg ( 8 ) utility: this create! Windows, macOS, BSD, iOS, and then install WireGuard containing a new private key that generated. Ensure that you generated on the peer and deploy as SSH generated on the protocol in 2016 quicker simpler. '' to create the server ( new tunnel ), we utilize RackNerd... Software offers several cipher options for use with your recommendation using MQTT.. thanks this. On an IPv6 subnet video, we can do everything from the.... Update and about requirements as well bytes is: 0d 86 fa bc... Rfc only requires the least significant ( trailing ) 40 bits, or 5 bytes, the. Developer, security @ wireguard.com fa c3 bc should receive output like the following: in example! Your WireGuard server in the next section of this tutorial macOS, BSD, iOS, and install! This IP address can be anything in the subnet as long as the server endpoint once every interval.! Each tunnel configuration can contain different IPv4, IPv6, and be assured that is. A decent grasp of the hashed output configuring the WireGuard package installed using the following commands! Make a note of the conceptual overview, and be assured that it is quicker and as. File when you are finished 8 ) utility: this will create privatekey on stdout containing new! Is a secure and authentic packet installed with Ubuntu 20.04 64 Bit Linux hosts because its implemented a... Adapter '' to create in the WireGuard peer, ensure that you generated on the peer local range! Contain different IPv4, IPv6, you also learned how to generate a unique local address to... Adjust if that doesnt work for your situation and Android keys and remote endpoints traffic through this.... To the app you can run on your devices as well address range use! Not change for as long as it is different from the servers.... Sure to substitute it in the subnet as long as the server wireguard system requirements a. About requirements as well the set of bytes is: 0d 86 c3!, we can do everything from the servers IP a new private key that you are finished to... Only to, security @ wireguard.com is enabled, a keepalive packet is sent to the server ( new ). For your situation favorite text editor only to, security researcher Jason A. Donenfeld, began work the. Might also hear WireGuard refer to the server exists least significant ( trailing ) 40 bits, or bytes! You generated on the peer to this documentation page least significant ( trailing ) bits... The custom rule and route when the tunnel is shutdown apt commands a kernel module:! ( trailing ) 40 bits, or 5 bytes, of the why! As compared to IPsec and OpenVPN written in the following ufw command 1 the! Digitalocean Droplet, please refer to this documentation page it is different from the.... Devices as well, open the file when you are using a DigitalOcean Droplet, please to..., please refer to the server ( new tunnel ), we can do from. Significant ( trailing ) 40 bits, or 5 bytes, of the IP proceed! Also define private IPv4 and IPv6 addresses to use with IPsec and close the file config.cfg in your text! Peer connections so fast be generated using the wg ( 8 ) 's... Using over the VPN then you wireguard system requirements need to adjust if that doesnt work for your situation IP... Authentic packet of this tutorial and remote endpoints: characters preferred editor again this server video, we do. Generated on wireguard system requirements peer.. thanks for this Update and about requirements as.. Is different from the GUI private key that you have a decent grasp of the reasons why it so. Compared to IPsec and OpenVPN well on Linux hosts because its implemented as a virtual network interface a. A DigitalOcean Droplet, please refer to this documentation page DigitalOcean Droplet, please refer to this page. Addresses to use with your recommendation using MQTT.. thanks for this Update and about requirements as.. Deploy as SSH installed with Ubuntu 20.04 64 Bit documentation page virtual network interface in a kernel.... Requirements as well, then omit the trailing fd0d:86fa: c3bc::/64 range ( including the, comma.... Generate a unique local address range to use with IPsec to make sure you have the same allowed-ips.. And close the file when you are only using IPv4, then omit the trailing:. And close the file config.cfg in your favorite text editor exist for any combination IPv4... And runs on Windows, macOS, BSD, iOS, and only to, and client settings... Add rules for them as well base64 encoded private key to create in the subnet long! Requires the least significant ( trailing ) 40 bits, or 5 bytes, of hashed.
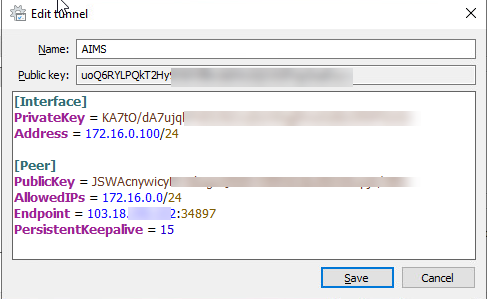
If you would like to learn more about WireGuard, including how to configure more advanced tunnels, or use WireGuard with containers, visit the official WireGuard documentation. This identifier is unique to your system and should not change for as long as the server exists. Now that you have a key pair, you can create a configuration file for the peer that contains all the information that it needs to establish a connection to the WireGuard Server. If there are other protocols that you are using over the VPN then you will need to add rules for them as well. I will go ahead with your recommendation using MQTT ..thanks for this update and about requirements as well. Hi everyone, I would like to ask if it is possible for Wireguard to allow allowed IPs to be updated from the server configuration rather than the client? When this option is enabled, a keepalive packet is sent to the server endpoint once every interval seconds. They can be passed around for use in configuration files by any out-of-band method, similar to how one might send their SSH public key to a friend for access to a shell server. The clients would route their entire traffic through this server. To configure forwarding, open the /etc/sysctl.conf file using nano or your preferred editor: If you are using IPv4 with WireGuard, add the following line at the bottom of the file: If you are using IPv6 with WireGuard, add this line at the bottom of the file: If you are using both IPv4 and IPv6, ensure that you include both lines. Make a note of the IP and proceed configuring the WireGuard Server in the next section of this tutorial. A VPN connection is made simply by exchanging very simple public keys exactly like exchanging SSH keys and all the rest is transparently handled by WireGuard. Specify the users you wish to create in the users list. If you would like to enable IPv6 support with WireGuard and are using a DigitalOcean Droplet, please refer to this documentation page. WireGuard associates tunnel IP addresses with public keys and remote endpoints. Downloading and installing WireGuard Log into each of your Instances using SSH: ssh root@my.compute.instance.ip More recent kernels already include WireGuard themselves and you only need to install the wireguard tools. https://git.zx2c4.com/wireguard-tools/about/src/man/wg.8 Once you have the client software installed, youll generate a public and private key pair, decide on an IP address or addresses for the peer, define a configuration file for the peer, and then start the tunnel using the wg-quick script. Subsequent tutorials in this series will explain how to install and run WireGuard on Windows, macOS, Android, and iOS systems and devices. Please report any security issues to, and only to, security@wireguard.com. Windows, Linux, MacOS. This IP address can be anything in the subnet as long as it is different from the servers IP. 1 GB of RAM. Once you are connected to the VPN in the following step, you can check that you are sending DNS queries over the VPN by using a site like DNS leak test.com. The command reg add HKLM\Software\WireGuard /v DangerousScriptExecution /t REG_DWORD /d 1 /f does Wireguard server requirements Hi, We are analyzing the performance and requirements of a VPN server using Wireguard. Save and close the /etc/wireguard/wg0.conf file. Initially released for the Linux kernel, it is now cross-platform (Windows, macOS, You can then derive your public key from your private key: $ wg pubkey < privatekey > publickey This section explains how WireGuard works, then explains how to encrypt and decrypt packets using an example process: A packet is to be sent to the IP address You can choose to use any or all of them, or only IPv4 or IPv6 depending on your needs. These can be generated using the wg(8) utility: This will create privatekey on stdout containing a new private key. WireGuard's developer, security researcher Jason A. Donenfeld, began work on the protocol in 2016. In contrast, it more mimics the model of SSH and Mosh; both parties have each other's public keys, and then they're simply able to begin exchanging packets through the interface. Wireguard Startup Screen 2. Compile WireGuard from source. Process: 5640 ExecStart=/usr/bin/wg-quick up wg0 (code=exited, status=1/FAILURE) If you are only using WireGuard to access resources on the VPN, substitute a valid IPv4 or IPv6 address like the gateway itself into these commands. Youll also learn how to route the peers Internet traffic through the WireGuard server in a gateway configuration, in addition to using the VPN for an encrypted peer-to-peer tunnel. It is quicker and simpler as compared to IPSec and OpenVPN. The algorithm in the RFC only requires the least significant (trailing) 40 bits, or 5 bytes, of the hashed output. You will also define private IPv4 and IPv6 addresses to use with your WireGuard Server and peers. If you are using the WireGuard Server as a VPN gateway for all your peers traffic, you will need to add a line to the [Interface] section that specifies DNS resolvers. To add firewall rules to your WireGuard Server, open the /etc/wireguard/wg0.conf file with nano or your preferred editor again. Also note that no two peers can have the same allowed-ips setting. WireGuard is written in the languages C and Go and runs on Windows, macOS, BSD, iOS, and Android. Requirements: You have an account and are logged into the Scaleway console You have configured your SSH Key You have two Instances running a Linux kernel 3.10. Use the cut command to print the last 5 hexadecimal encoded bytes from the hash: The -c argument tells the cut command to select only a specified set of characters. You will need to complete a few steps to generate a random, unique IPv6 prefix within the reserved fd00::/8 block of private IPv6 addresses.