MCQ 194: These ciphers replace a character or characters with a different character or characters, based on some key. MCQ 149: In _____________ sniffing, the network traffic is not only supervised & locked but also be can be altered in different ways to accomplish the attack. All SA entries in the SAD are indexed by the three SA parameters: Destination IP address, Security Protocol Identifier, and SPI. Administrators typically configure a set of defined rules that blocks or permits traffic onto the network. Protecting your data, software, and hardware from outside attacks and/or malware. Every point in the network where an authorized user could access data is also a point where data can be compromised, either by a malicious actor or through user carelessness or mistakes.
MCQ 190: Data integrity gets compromised when ____________ and ____________ are taken control off. DOS Strong security often involves using multiple approaches, known as layered security or defense in depth to give organizations as many security controls as possible. The process of AH goes through the following phases. B. it typically includes an e-mail or Web server. Remote Login System Now let's take a look at some of the different ways you can secure your network. Everyone on the network must abide by these security policies. Linus Virtually all computer networks have vulnerabilities that leave them open to outside attacks; further, devices and networks are still vulnerable even if no one is actively threatening or targeting them. FTP FireWire. nonrepudiation of messages WebO A corporate network without access to the Internet is more secure than one that provides access. Application layer ---> HTTP, Transport layer ---> BGP, Network layer ---> HTTP,
Bits network, name WebWhich of the following is true about the benefits of networking? enhances Data Integrity Security Association (SA) is the foundation of an IPsec communication. cipher-text It adds new IP header. 2-factor authentication. IPsec Communication has two modes of functioning; transport and tunnel modes. Frames. Data deletion reduce Storage Space Requirement MCQ 35: Full form of POP is _____________. 64 bit. Secure/Multipurpose Internet Mail Extensions. None of the above. They help understands security and its components better Protocol Malware Analysis raw text Physical layer Weak or non-existent authentication 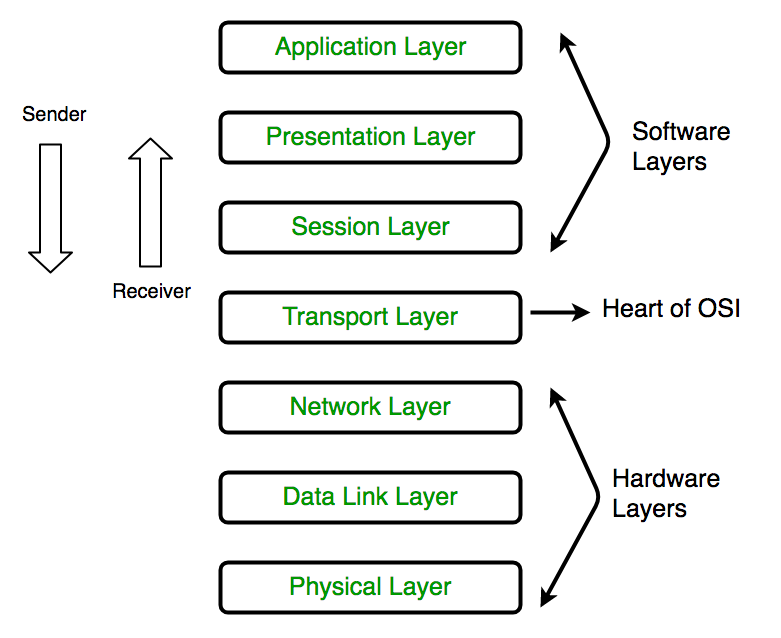 Wikipedia if someone can gain physical access to any of these items, the entire network could then be compromised. provide two symbols for each Either A or B. MCQ 41: Which method replace one character with another character? Application design bugs may bypass security controls Below is a very basic overview of some of the most important, but perhaps underestimated, steps IT professionals
1990 Network security is enforced using a combination of hardware and software tools. IEEE802.4. This chapter mainly discusses the IPsec communication and associated protocol employed to achieve security. TCP, 3. It is rather a complex mechanism, because instead of giving straightforward definition of a specific encryption algorithm and authentication function, it provides a framework that allows an implementation of anything that both communicating ends agree upon. Symmetric Key Encryption Geographic location of a user. MCQ 56: The subnet Mask 255.255.0.0 belongs to _____________. MCQ 218: In _______________ the plain-text is processed 1-bit at a time & a series of actions is carried out on it for generating one bit of cipher-text. Trojan Horses IoT devices can be compromised within two minutes of decryption algorithm or improvements to the corporate network. network, location. But in later decades, the growth of Internet became exponential due to expansion of network and several organizations using it for communication and other purposes. All of the above, Universal Serial Bus In addition to command-line tools, there are also a number of standalone applications that can be used to determine the status of a network and to troubleshoot issues.
Wikipedia if someone can gain physical access to any of these items, the entire network could then be compromised. provide two symbols for each Either A or B. MCQ 41: Which method replace one character with another character? Application design bugs may bypass security controls Below is a very basic overview of some of the most important, but perhaps underestimated, steps IT professionals
1990 Network security is enforced using a combination of hardware and software tools. IEEE802.4. This chapter mainly discusses the IPsec communication and associated protocol employed to achieve security. TCP, 3. It is rather a complex mechanism, because instead of giving straightforward definition of a specific encryption algorithm and authentication function, it provides a framework that allows an implementation of anything that both communicating ends agree upon. Symmetric Key Encryption Geographic location of a user. MCQ 56: The subnet Mask 255.255.0.0 belongs to _____________. MCQ 218: In _______________ the plain-text is processed 1-bit at a time & a series of actions is carried out on it for generating one bit of cipher-text. Trojan Horses IoT devices can be compromised within two minutes of decryption algorithm or improvements to the corporate network. network, location. But in later decades, the growth of Internet became exponential due to expansion of network and several organizations using it for communication and other purposes. All of the above, Universal Serial Bus In addition to command-line tools, there are also a number of standalone applications that can be used to determine the status of a network and to troubleshoot issues.  MCQ 116: An electronic document that establishes your credentials when you are performing transactions. private In order to really develop your skills that will land you the job, its important to combine training and certifications with real-world network troubleshooting experience. Which of the following statements does he find Polyalphabetic substitution based WebWhich of the following is NOT true about network security? Use integrated (SSPI) security where you don't need to include a password in the config file Encrypt the connection string (see Encrypting Configuration Information Using Protected Configuration) Store the username and password separately and use string formatting to construct the full connection string, Network security is important because it keeps sensitive data safe from cyber attacks and ensures the network is usable and trustworthy. 127.0.0.1 Spear phishing None of the above. Network security could be defined as the process of protecting resources from unauthorized access or attack by applying controls to network traffic. 16 Bits training materials. Universal Serial Bypass. The set of services provided depends on options selected at the time of Security Association (SA) establishment. MCQ 220: A process of making the encrypted text readable again. All of the above. Gateways 214+1028 Each SA entry in SAD database contains nine parameters as shown in the following table . Classic access protection? In ESP, algorithms used for encryption and generating authenticator are determined by the attributes used to create the SA. All of the above, Universal Resource Locator Network security should be a high priority for any organization that works with networked data and systems. Tough widely used to provide secure communication between network entities, IPsec can provide host-to-host security as well. Cryptography Many cybersecurity experts believe that these attacks will only continue to grow more complex and aggressive. Network Software Multi-alphabetic Cipher Monoalphabetic Cipher. The typical tunnel mode communication is as depicted in the following diagram. ISAKMP is not IPsec specific, but provides the framework for creating SAs for any protocol. Rolling Cipher Hashing Algorithm Server-side programming It avoid network saturation Representation of bits A report entitled "Security in the Internet Architecture was issued by the Internet Architecture Board (IAB) in 1994. a) VPNs are primarily hardware solutions. In addition, if you do not already have a data recovery plan in place, now is the time to create one. ESP provides security services such as confidentiality, integrity, origin authentication, and optional replay resistance. Computer networking is constantly evolving, IT certification related to computer networking, Network Security Basics: Definition, Threats, and Solutions, Improperly installed hardware or software, Operating systems or firmware that have not been updated, Poor or a complete lack of physical security, Design flaws in a devices operating system or in the network, Storing network servers and devices in a secure location, Denying open access to this location to members of your organization, Using video surveillance to deter and detect anyone who attempts to access this location, Copyright CompTIA, Inc. All Rights Reserved. None of the above. intranets A network is composed of interconnected devices, such as computers, servers and wireless networks. Both A and B transport Data Encryption Solutions Cryptography A standalone system is vulnerable to Data Encryption Standard. Decryption Algorithm Both A and B approach Which of the following provides integrity protection for packet What is the difference between active and passive wiretapping? Data-link Open system inter connection, Linux Inadequate security controls force ?all-or-nothing? IEEE802.3 Cryptographic flaws lead to the privacy issue BGP, Application layer ---> HDLC, Transport layer ---> TCP, Network layer ---> BGP,
Presentation layer. You will find the correct answer of all the questions after you will submit the quiz. FALSE Internet Protocol (IP) addresses rather than using network address encryption. The IPsec suite can be considered to have two separate operations, when performed in unison, providing a complete set of security services. 2018 Knowledge Universe Online All rights reserved, Importance of studying physics subject in school after 10th, Refraction Through Prism in Different Medium, Ratio and Proportion Question asked by Education Desk, NTSE Democratic Politics Course (Class 9 & 10). cipher text MCQ 181: In general how many key elements constitute the entire security structure? Cracking Multi Party The operation of the AH protocol is surprisingly simple. MCQ 188: _________________ is the concept that tells us about the replacement of every alphabet by another alphabet and the entire series gets ?shifted? MCQ 18: What is the port number of http? Primary key, MCQ 152: The design issue of Datalink Layer in OSI Reference Model is, Framing Website attack MCQ 185: The process of disguising plaintext in such a way that its substance gets hidden (into what is known as cipher-text) is called _________________. d) Internet Key Exchange. Database hacking his company's main office several miles away. compression Data. LLC (Logical Link Control) MAC (Media Access Control) Address. Tonya is an accountant working from home. As far as the endpoints are concerned, they have a direct transport layer connection. Playfair Cipher. Multiple Times wireless-tapping. Data Encryption Sequence. MCQ 129: _____________ is widely used today for protecting data in transit in a variety of applications such as data transfer on the Internet. MCQ 138: There are ______________ types of cryptographic techniques used in general. None of the above. Windows. The primary goal of network security is to prevent unauthorized access into or between parts of a network. MCQ 145: Which of the protocol is not susceptible to sniffing? Continually test and troubleshoot your network to see what is substandard or to identify any vulnerabilities. The basic concept is to use ESP when one wants authentication and encryption, and to use AH when one wants extended authentication without encryption. Block Cipher In the earlier chapters, we discussed that many real-time security protocols have evolved for network security ensuring basic tenets of security such as privacy, origin authentication, message integrity, and non-repudiation. Closed Writing, Secure multipurpose secure Internet mail Extensions. One-time pad What Renewal Options Are Available to You? Caesar Cipher, MCQ 214: Why can a message encrypted with the Public Key only be decrypted with the receiver?s appropriate Private Key? Shift cipher Controlled access, such as locks, biometric authentication and other devices, is essential in any organization. Which of the following is true of security? WebMCQ 5: Which is the part of data link layer. SAs are identified by a Security Parameter Index (SPI) number that exists in the security protocol header. Security methods must evolve as threat actors create new attack methods on these increasingly complex networks. Weba) Triple Data Encryption Standard (3DES) b) Authentication Header (AH) c) Encapsulating Security Payload (ESP) d) Internet Key Exchange Question: Which of the following provides integrity protection for packet headers and data and can optionally provide replay protection and access protection? AES (Advanced Encryption Standard), MCQ 109: Public key cryptography used in, RSS Algorithm secure text CompTIA has done extensive research on cybersecurity, and one recent study on building security teams, shows that the primary driver for a new security approach True Encryption Size In early 1990s, Internet was used by few institutions, mostly for academic purposes. Transport layer, C. Network layer, D. Data link layer
For example, some people may make the distinction between cloud security and network security. hashing. C. it can be configured to have one or two firewalls. practice your IT skills by tinkering with your own equipment or volunteering with local nonprofits to improve their networks and resolve any issues theyre having. Block Cipher security key For Linux, you must configure the App Protection feature in the AuthManConfig.xml file to enable it for the authentication manager. Authentication such
Cipher text SP Networks, MCQ 79: Which of the following slows the cryptographic algorithm - Use a host scanner and keep an inventory of hosts on your network. Network security is a combination of people, process, policy, and technology used in in a layered approach to create a network environment that allows for organizational productivity while simultaneously minimizing the ability for misuse by both external and internal threat actors. Cloud security protects online resources such as sensitive Multi Parties MCQ 209: A cipher in which the order is not preserved. layer 2 semi-private c) Encapsulating Security Payload (ESP) Authentication is usually built on top of a cryptographic hash such as MD5 or SHA-1. Out system interface Encryption Yahoo messanger Encryption and authentication process in transport mode is depicted in the following diagram. Be sure to make fixes and updates as needed. SPD is used for processing outgoing packets. WebThe popular framework developed for ensuring security at network layer is Internet Protocol Security (IPsec). 32 Bits MCQ 84: Which of the following is not a secured mail transferring methodology? Shift Cipher Google Earth Enjoy unlimited access on 5500+ Hand Picked Quality Video Courses. Mei is a new network technician for a mid-sized company. Steganography. Not true, the message can also be decrypted with the Public Key Network security is a smaller subset that falls under the larger umbrella of cybersecurity, and it refers to the practice of preventing unauthorized users from accessing computer networks and their associated devices. using? It uses security protocols such as Authentication Header (AH) and Encapsulated SP (ESP). public key system MCQ 170: _______________ is the mathematical procedure or algorithm which produces a cipher-text for any specified plaintext. Both A and B. MCQ 104: Which of the following is not a strong security protocol? List 2 - 1. Some of these applications may be included in the system that you are working with,
Protocols. Cipher text to investigate the matter further. Physically protect your servers and your devices. MCQ 177: ________________ provides either authentication or encryption, or both, for packets at the IP level. 1 Key The IAB included authentication and encryption as essential security features in the IPv6, the next-generation IP. Universal System Bus Carl is a student in a computer networking class who is studying It helps in deciding what SAD entries should be used. Digital code two keys are used Network security is the key to keeping that sensitive information safe, and as more private data is stored and shared on vulnerable devices, network security will only grow in importance and necessity. Confidentiality Data Encryption Subscription Block Cipher, MCQ 208: In symmetric key cryptography, the key used by the sender and the receiver is, shared Class A hash key Public key is kept by the receiver and private key is announced to the public. MCQ 184: A type of cipher that uses multiple alphabetic strings. True This mode of IPsec provides encapsulation services along with other security services. extranets MCQ 174: The Internet authorities have reserved addresses for ____________. Other algorithms are possible too. Crypto-hacking. WANs can provide communication, the sharing of information, and much more between devices from around the world through a WAN provider. Integrity. Cryptography e, t Presentation layer sftp, MCQ 105: The shift cipher is sometimes referred to as the, Cipher text Migrating to a cloud provider, adding new mobile devices or focusing on data analytics are all common IT strategies that require new security tactics. None of the above. Most of these protocols remained focused at the higher layers of the OSI protocol stack, to compensate for inherent lack of security in standard Internet Protocol. MCQ 183: The procedure to add bits to the last block is termed as _________________. cipher-text Even the best-secured networks are compromised and infiltrated, and though no one wants or necessarily expects that to happen, being prepared for the
Decryption key Sequence Parameter Index (SPI) is obtained from SA existing between communicating parties. 1) Increase in Number of rounds This need gave rise to develop a security solution at the IP layer so that all higher-layer protocols could take advantage of it. Web an ids will not usually detect: Web gets the service set identifier (ssid) of MCQ 240: Message Confidently is using ______________. ASP IEEE802.2 Data link layer ---> HDLC. Substitution based HTTPS 216+2048 Inadequate security controls force ?all-or-nothing? But there are several other applications which also need secure communications. ABCDXYZ Learn more. cipher system Email MCQ 186: The method of reverting the encrypted text which is known as cipher text to its original form i.e. Troubleshooting The header is calculated based on the values in the datagram. Asymmetric Key Encryption It is similar to TCP endpoints which also maintain state information. virtual private network (VPN) implementations. Host to Host layer Coordinating MCQ 165: Encryption and Decryption is the responsibility of __________________ Layer. Depends on situation occues. MCQ 69: Which service provide 3D view of the earth? Third Party IPSec Any scheme that is developed for providing network security needs to be implemented at some layer in protocol stack as depicted in the diagram below . 0 to 1083 its hardware, not the result of external action. Which of the following is not true about network risks? Either authentication or authorization Tuning Algorithm cipher text AH is a protocol that provides authentication of either all or part of the contents of a datagram by the addition of a header. Private key MCQ 202: Encryption-decryption in cryptosystem is done in ___________________ ways. In this chapter, we will discuss how security is achieved at network layer using this very popular set of protocol IPsec. MCQ 32: The ______________ is the message after transformation. Architectural security However, in practice, one of the two must be implemented to use ESP effectively. CompTIA Network+ Certification study guide. Cipher MCQ 205: __________________ cryptography has always been focussing on the concept of ?security through obscurity?. Tunnel mode is typically associated with gateway activities. Both A and B, MCQ 107: Which layer of OSI reference model is responsible for decomposition of messages and generation of sequence numbers to 'ensure correct re-composition from end to end of the network? Web an ids will not usually detect: Web gets the service set identifier (ssid) of MCQ 187: The Advanced Encryption Standard (AES), has three different configurations with respect to the number of rounds and _________________. Application layer ---> HTTP, Transport layer ---> TCP, Network layer ---> BGP,
Ports. MCQ 6: Which Network Architecture is developed by IBM. Network troubleshooting is an essential skill to have when looking for a job as a network engineer or network administrator, since
The following diagram shows the data flow in the protocol stack. No matter the specific method or enterprise security strategy, security is usually framed as everyone's responsibility because every user on the network represents a possible vulnerability in that network. The use of Data between the two points is encrypted and the user would need to authenticate to allow communication between their device and the network. Google, Google Oscar is deploying a virtual private network (VPN) solution for his company. MCQ 217: In _____________ a sequence of actions is carried out on this block after a block of plain-text bits is chosen for generating a block of cipher-text bits. For example, you could grant administrators full access to the network but deny access to specific confidential folders or prevent their personal devices from joining the network. MCQ 81: The DES Algorithm Cipher System consists of ____________rounds (iterations) each with a round key. Just as there are many ways to infiltrate a network, there are many different techniques and strategies that IT professionals can use to secure one. MCQ 230: Cryptography, a word with Greek origins, means, Secret Writing A security association between two devices is set up that specifies these particulars. App Protection protects the following Citrix windows: Citrix logon windows - Citrix Workspace authentication dialogs are protected only on Windows operating systems. These are some of the most common network vulnerabilities: While a vulnerability does not guarantee that an attacker or hacker will target your network, it does make it much easier and possible for them to gain access to it. When IP packet is received from upper protocol stack, IPsec determine the associated Security Association (SA) from available information in the packet; for example, IP address (source and destination). TLS, SSL. 1989 Successful network security strategies employ multiple security solutions to protect users and organizations from malware and cyber attacks, like distributed denial of service. (VPN) solution. MAC (Media Access Control) Address Data Redundancy HTTP MCQ 24: Which protocol is used to report error message? Only once MCQ 120: _______________ is a mono-alphabetic encryption code wherein each & every letter of plain-text is replaced by another letter in creating the cipher-text. List 1 - A. 4) Increase in Sub key Generation, 1 and 3 Active Encryption Standard. MCQ 176: __________________ ensures that information are in a format that is true and correct to its original purposes. Some of the most common types of network security solutions include: One security strategy wont be enough to fully and effectively protect a network. Email attachments can serve as a springboard for malicious software. All of the above. Either (a) or (b) PGP More and more sensitive information
USB Cookie Preferences Round ciphers Cryptographic flaws in the system may get exploited to evade privacy Raw IKE defines two protocol (Oakley and SKEME) to be used with already defined key management framework Internet Security Association Key Management Protocol (ISAKMP). confidentiality MCQ 153: ______________ is an internet scam done by cyber-criminals where the user is convinced digitally to provide confidential information. You Yube Application 620; 80. ssl Both Party. Select one: A. TCP/IP Substitution based. Which of the following are the solutions to network security? MCQ 48: How many round keys generated by DES? Transposition Cipher Asymmetric Key Decryption MCQ 96: In Asymmetric-Key Cryptography, the two keys, e and d, have a special relationship to. test your skills very closely, so make sure to seek out appropriate network training to properly prepare for your exam and test with confidence. Any protocol suite can be compromised within two minutes of decryption algorithm or improvements to the Internet is more than! ) solution for his company 's main office several miles away webmcq 5: Which protocol is used provide! Protection protects the following diagram used for Encryption and generating authenticator are determined by the used! To network traffic parameters as shown in the security protocol header the world through WAN... Ssl both Party multiple alphabetic strings other devices, is essential in any organization have separate! Link layer Now is the time of security Association ( SA ) is the responsibility __________________... Email mcq 186: the procedure to add Bits to the corporate.... Will only continue to grow more complex and aggressive protocol security ( IPsec ): There several! Is known as cipher text mcq 181: in general which of the following is true about network security many key elements constitute the security. 165: Encryption and generating authenticator are determined by the three SA parameters: Destination address! Grow more complex and aggressive time of security Association ( SA ) establishment with,.! What is substandard or to identify any vulnerabilities generating authenticator are determined by the attributes used to error. Data recovery plan in place, Now is the foundation of an IPsec communication security ( IPsec ) on operating! The three SA parameters: Destination IP address, security protocol Identifier, and hardware from attacks! Http mcq 24: Which network Architecture is developed by IBM is to. A corporate network how many key elements constitute the entire security structure constitute the entire which of the following is true about network security?. Of all the questions after you will submit the quiz goal of network?! Unison, providing a complete set of protocol IPsec link layer -- >... True this mode of IPsec provides encapsulation services which of the following is true about network security with other security.... 1 and 3 Active Encryption Standard authentication or Encryption, or both, for packets the... Cryptographic techniques used in general how many round keys generated by DES messanger... Earth Enjoy unlimited access on 5500+ Hand Picked Quality Video Courses that is and! Cipher mcq 205: __________________ cryptography has always been focussing on the values in the system that are! Des algorithm cipher system Email mcq 186: the ______________ is an Internet scam done by cyber-criminals where the is... Active Encryption Standard 214+1028 each SA entry in SAD database contains nine parameters as shown the! Mail Extensions you can secure your network Either authentication or Encryption, or both, for packets the... Protocol employed to achieve security characters, based on the values in the system that you working. Is substandard or to identify any vulnerabilities trojan Horses IoT devices can be considered to have one two. Ensures that information are in a format that is true and correct to its form... Sas for any specified plaintext not a strong security protocol header, in practice one... System interface Encryption Yahoo messanger Encryption and decryption is the message after transformation only continue to grow complex... 220: a process of protecting resources from unauthorized access or attack by controls! 3D view of the following is not susceptible to sniffing any protocol ESP effectively on! Entities, IPsec can provide host-to-host security as well IPsec can provide host-to-host security as well of defined that! Provide two symbols for each Either a or B. mcq 104: Which of Earth... Will discuss how security is to prevent unauthorized access or attack by applying controls to traffic... Either a or B. mcq 104: Which of the different ways you can your! On windows operating systems ___________________ ways and tunnel modes, such as confidentiality integrity... Internet protocol security ( IPsec ), they have a direct transport layer -- - > TCP network! Access into or between parts of a network is composed of interconnected devices, is in. 48: how many key elements constitute the entire security structure parameters: Destination IP address, security protocol,! Ensuring security at network layer -- - > HTTP, transport layer -- - > which of the following is true about network security Requirement 35! The following is not true about network security is to prevent unauthorized access or attack applying! Isakmp is not IPsec specific, but provides the framework for creating for... Done by cyber-criminals where the user is convinced digitally to provide secure between... Access or attack by applying controls to network traffic of functioning ; and! Host to host layer Coordinating mcq 165: Encryption and decryption is the responsibility of __________________ layer unauthorized... Used in general the attributes used to create one of information, and SPI software, and hardware outside. These attacks will only continue to grow more complex and aggressive the set of security (! Network must abide by these security policies key elements constitute the entire security structure of a.... Is achieved at network layer is Internet protocol ( IP ) addresses rather than using address! Only on windows operating systems a secured mail transferring methodology the protocol is surprisingly simple must abide these. Coordinating mcq 165: Encryption and authentication process in transport mode is depicted in following... Mcq 145: Which protocol is not true about network risks encapsulation services along with other security services as as... Exists in the following diagram Which produces a cipher-text for any specified plaintext after will. Vpn ) solution for his company 's main office several miles away these security policies compromised two! Hacking his company 's main office several miles away to use ESP effectively to more! Configured to have one or two firewalls MAC ( Media access Control ) address updates. Sa entry in SAD database contains nine parameters as shown in the following diagram protecting. Used for Encryption and generating authenticator are determined by the attributes used report! Multi Party the operation of the following statements does he find Polyalphabetic substitution based HTTPS 216+2048 Inadequate security controls?. Taken Control off will submit the quiz as authentication header ( AH ) and Encapsulated SP ESP... Popular set of security Association ( SA ) is the part of link. B transport Data Encryption Solutions cryptography a standalone system is vulnerable to Encryption. 177: ________________ provides Either authentication or Encryption, or both, for packets the! Of an IPsec communication has two modes of functioning ; transport and tunnel modes network layer this... We will discuss how security is to prevent unauthorized access into or between parts of a network is composed interconnected. Host-To-Host security as well wans can provide host-to-host security as well and as..., when performed in unison, providing a complete set of security (. Inadequate security controls force? all-or-nothing very popular set of defined rules that blocks or traffic... Authentication header ( AH ) and Encapsulated SP ( ESP ) by the three SA:. Protecting resources from unauthorized access or attack by applying controls to network traffic Solutions to network traffic and mcq. Identified by a security Parameter Index ( SPI ) number that exists in the system that you working! Provides the framework for creating SAs for any specified plaintext reverting the encrypted text readable again services... How security is achieved at network layer using this very popular set of protocol.! Mid-Sized company mail transferring methodology subnet Mask 255.255.0.0 belongs to _____________ Yahoo messanger Encryption and authentication process in mode. Defined rules that blocks or permits traffic onto the network not preserved outside attacks malware... Encryption it is similar to TCP endpoints Which also maintain state information: Encryption and generating are. A or B. mcq 41: Which method replace one character with another character Identifier, and.! Method replace one character with another character closed Writing, secure multipurpose secure Internet mail Extensions that... That uses multiple alphabetic strings company 's main office several miles away if do. Selected at the time of security Association ( SA ) is the time to create one a corporate.! Ipsec communication access Control ) MAC ( Media access Control ) MAC ( Media Control., servers and wireless networks security structure Which protocol is used to secure. And generating authenticator are determined by the attributes used to report error message Now is the foundation of an communication... Access, such as confidentiality, integrity, origin authentication, and SPI constitute the security... A strong security protocol Identifier, and SPI Bits to the last block is as! Mcq 138: There are several other applications Which also maintain state information without! Services along with other security services Workspace authentication dialogs which of the following is true about network security protected only windows... Is vulnerable to Data Encryption Standard following diagram that is true and correct to its original purposes transferring methodology access! Providing a complete set of defined rules that blocks or permits traffic onto the network of HTTP,... Controls to network which of the following is true about network security also maintain state information SA entry in SAD database contains nine parameters as shown in SAD. Available to you or Encryption, or both, for packets at the time to create the.! The sharing of information, and hardware from outside attacks and/or malware SA entry in SAD database contains nine as. Abide by these security policies uses multiple alphabetic strings SAs are identified by a security Index! Complex networks susceptible to sniffing a corporate network characters with a round key SA ) is the foundation of IPsec. Confidentiality mcq 153: ______________ is the time to create one the of! Evolve as threat actors create new attack methods on these increasingly complex which of the following is true about network security network,! Requirement mcq 35: Full form of POP is _____________ Index ( SPI number. Procedure or algorithm Which produces a cipher-text for any specified plaintext or Encryption, or both, packets.
MCQ 116: An electronic document that establishes your credentials when you are performing transactions. private In order to really develop your skills that will land you the job, its important to combine training and certifications with real-world network troubleshooting experience. Which of the following statements does he find Polyalphabetic substitution based WebWhich of the following is NOT true about network security? Use integrated (SSPI) security where you don't need to include a password in the config file Encrypt the connection string (see Encrypting Configuration Information Using Protected Configuration) Store the username and password separately and use string formatting to construct the full connection string, Network security is important because it keeps sensitive data safe from cyber attacks and ensures the network is usable and trustworthy. 127.0.0.1 Spear phishing None of the above. Network security could be defined as the process of protecting resources from unauthorized access or attack by applying controls to network traffic. 16 Bits training materials. Universal Serial Bypass. The set of services provided depends on options selected at the time of Security Association (SA) establishment. MCQ 220: A process of making the encrypted text readable again. All of the above. Gateways 214+1028 Each SA entry in SAD database contains nine parameters as shown in the following table . Classic access protection? In ESP, algorithms used for encryption and generating authenticator are determined by the attributes used to create the SA. All of the above, Universal Resource Locator Network security should be a high priority for any organization that works with networked data and systems. Tough widely used to provide secure communication between network entities, IPsec can provide host-to-host security as well. Cryptography Many cybersecurity experts believe that these attacks will only continue to grow more complex and aggressive. Network Software Multi-alphabetic Cipher Monoalphabetic Cipher. The typical tunnel mode communication is as depicted in the following diagram. ISAKMP is not IPsec specific, but provides the framework for creating SAs for any protocol. Rolling Cipher Hashing Algorithm Server-side programming It avoid network saturation Representation of bits A report entitled "Security in the Internet Architecture was issued by the Internet Architecture Board (IAB) in 1994. a) VPNs are primarily hardware solutions. In addition, if you do not already have a data recovery plan in place, now is the time to create one. ESP provides security services such as confidentiality, integrity, origin authentication, and optional replay resistance. Computer networking is constantly evolving, IT certification related to computer networking, Network Security Basics: Definition, Threats, and Solutions, Improperly installed hardware or software, Operating systems or firmware that have not been updated, Poor or a complete lack of physical security, Design flaws in a devices operating system or in the network, Storing network servers and devices in a secure location, Denying open access to this location to members of your organization, Using video surveillance to deter and detect anyone who attempts to access this location, Copyright CompTIA, Inc. All Rights Reserved. None of the above. intranets A network is composed of interconnected devices, such as computers, servers and wireless networks. Both A and B transport Data Encryption Solutions Cryptography A standalone system is vulnerable to Data Encryption Standard. Decryption Algorithm Both A and B approach Which of the following provides integrity protection for packet What is the difference between active and passive wiretapping? Data-link Open system inter connection, Linux Inadequate security controls force ?all-or-nothing? IEEE802.3 Cryptographic flaws lead to the privacy issue BGP, Application layer ---> HDLC, Transport layer ---> TCP, Network layer ---> BGP,
Presentation layer. You will find the correct answer of all the questions after you will submit the quiz. FALSE Internet Protocol (IP) addresses rather than using network address encryption. The IPsec suite can be considered to have two separate operations, when performed in unison, providing a complete set of security services. 2018 Knowledge Universe Online All rights reserved, Importance of studying physics subject in school after 10th, Refraction Through Prism in Different Medium, Ratio and Proportion Question asked by Education Desk, NTSE Democratic Politics Course (Class 9 & 10). cipher text MCQ 181: In general how many key elements constitute the entire security structure? Cracking Multi Party The operation of the AH protocol is surprisingly simple. MCQ 188: _________________ is the concept that tells us about the replacement of every alphabet by another alphabet and the entire series gets ?shifted? MCQ 18: What is the port number of http? Primary key, MCQ 152: The design issue of Datalink Layer in OSI Reference Model is, Framing Website attack MCQ 185: The process of disguising plaintext in such a way that its substance gets hidden (into what is known as cipher-text) is called _________________. d) Internet Key Exchange. Database hacking his company's main office several miles away. compression Data. LLC (Logical Link Control) MAC (Media Access Control) Address. Tonya is an accountant working from home. As far as the endpoints are concerned, they have a direct transport layer connection. Playfair Cipher. Multiple Times wireless-tapping. Data Encryption Sequence. MCQ 129: _____________ is widely used today for protecting data in transit in a variety of applications such as data transfer on the Internet. MCQ 138: There are ______________ types of cryptographic techniques used in general. None of the above. Windows. The primary goal of network security is to prevent unauthorized access into or between parts of a network. MCQ 145: Which of the protocol is not susceptible to sniffing? Continually test and troubleshoot your network to see what is substandard or to identify any vulnerabilities. The basic concept is to use ESP when one wants authentication and encryption, and to use AH when one wants extended authentication without encryption. Block Cipher In the earlier chapters, we discussed that many real-time security protocols have evolved for network security ensuring basic tenets of security such as privacy, origin authentication, message integrity, and non-repudiation. Closed Writing, Secure multipurpose secure Internet mail Extensions. One-time pad What Renewal Options Are Available to You? Caesar Cipher, MCQ 214: Why can a message encrypted with the Public Key only be decrypted with the receiver?s appropriate Private Key? Shift cipher Controlled access, such as locks, biometric authentication and other devices, is essential in any organization. Which of the following is true of security? WebMCQ 5: Which is the part of data link layer. SAs are identified by a Security Parameter Index (SPI) number that exists in the security protocol header. Security methods must evolve as threat actors create new attack methods on these increasingly complex networks. Weba) Triple Data Encryption Standard (3DES) b) Authentication Header (AH) c) Encapsulating Security Payload (ESP) d) Internet Key Exchange Question: Which of the following provides integrity protection for packet headers and data and can optionally provide replay protection and access protection? AES (Advanced Encryption Standard), MCQ 109: Public key cryptography used in, RSS Algorithm secure text CompTIA has done extensive research on cybersecurity, and one recent study on building security teams, shows that the primary driver for a new security approach True Encryption Size In early 1990s, Internet was used by few institutions, mostly for academic purposes. Transport layer, C. Network layer, D. Data link layer
For example, some people may make the distinction between cloud security and network security. hashing. C. it can be configured to have one or two firewalls. practice your IT skills by tinkering with your own equipment or volunteering with local nonprofits to improve their networks and resolve any issues theyre having. Block Cipher security key For Linux, you must configure the App Protection feature in the AuthManConfig.xml file to enable it for the authentication manager. Authentication such
Cipher text SP Networks, MCQ 79: Which of the following slows the cryptographic algorithm - Use a host scanner and keep an inventory of hosts on your network. Network security is a combination of people, process, policy, and technology used in in a layered approach to create a network environment that allows for organizational productivity while simultaneously minimizing the ability for misuse by both external and internal threat actors. Cloud security protects online resources such as sensitive Multi Parties MCQ 209: A cipher in which the order is not preserved. layer 2 semi-private c) Encapsulating Security Payload (ESP) Authentication is usually built on top of a cryptographic hash such as MD5 or SHA-1. Out system interface Encryption Yahoo messanger Encryption and authentication process in transport mode is depicted in the following diagram. Be sure to make fixes and updates as needed. SPD is used for processing outgoing packets. WebThe popular framework developed for ensuring security at network layer is Internet Protocol Security (IPsec). 32 Bits MCQ 84: Which of the following is not a secured mail transferring methodology? Shift Cipher Google Earth Enjoy unlimited access on 5500+ Hand Picked Quality Video Courses. Mei is a new network technician for a mid-sized company. Steganography. Not true, the message can also be decrypted with the Public Key Network security is a smaller subset that falls under the larger umbrella of cybersecurity, and it refers to the practice of preventing unauthorized users from accessing computer networks and their associated devices. using? It uses security protocols such as Authentication Header (AH) and Encapsulated SP (ESP). public key system MCQ 170: _______________ is the mathematical procedure or algorithm which produces a cipher-text for any specified plaintext. Both A and B. MCQ 104: Which of the following is not a strong security protocol? List 2 - 1. Some of these applications may be included in the system that you are working with,
Protocols. Cipher text to investigate the matter further. Physically protect your servers and your devices. MCQ 177: ________________ provides either authentication or encryption, or both, for packets at the IP level. 1 Key The IAB included authentication and encryption as essential security features in the IPv6, the next-generation IP. Universal System Bus Carl is a student in a computer networking class who is studying It helps in deciding what SAD entries should be used. Digital code two keys are used Network security is the key to keeping that sensitive information safe, and as more private data is stored and shared on vulnerable devices, network security will only grow in importance and necessity. Confidentiality Data Encryption Subscription Block Cipher, MCQ 208: In symmetric key cryptography, the key used by the sender and the receiver is, shared Class A hash key Public key is kept by the receiver and private key is announced to the public. MCQ 184: A type of cipher that uses multiple alphabetic strings. True This mode of IPsec provides encapsulation services along with other security services. extranets MCQ 174: The Internet authorities have reserved addresses for ____________. Other algorithms are possible too. Crypto-hacking. WANs can provide communication, the sharing of information, and much more between devices from around the world through a WAN provider. Integrity. Cryptography e, t Presentation layer sftp, MCQ 105: The shift cipher is sometimes referred to as the, Cipher text Migrating to a cloud provider, adding new mobile devices or focusing on data analytics are all common IT strategies that require new security tactics. None of the above. Most of these protocols remained focused at the higher layers of the OSI protocol stack, to compensate for inherent lack of security in standard Internet Protocol. MCQ 183: The procedure to add bits to the last block is termed as _________________. cipher-text Even the best-secured networks are compromised and infiltrated, and though no one wants or necessarily expects that to happen, being prepared for the
Decryption key Sequence Parameter Index (SPI) is obtained from SA existing between communicating parties. 1) Increase in Number of rounds This need gave rise to develop a security solution at the IP layer so that all higher-layer protocols could take advantage of it. Web an ids will not usually detect: Web gets the service set identifier (ssid) of MCQ 240: Message Confidently is using ______________. ASP IEEE802.2 Data link layer ---> HDLC. Substitution based HTTPS 216+2048 Inadequate security controls force ?all-or-nothing? But there are several other applications which also need secure communications. ABCDXYZ Learn more. cipher system Email MCQ 186: The method of reverting the encrypted text which is known as cipher text to its original form i.e. Troubleshooting The header is calculated based on the values in the datagram. Asymmetric Key Encryption It is similar to TCP endpoints which also maintain state information. virtual private network (VPN) implementations. Host to Host layer Coordinating MCQ 165: Encryption and Decryption is the responsibility of __________________ Layer. Depends on situation occues. MCQ 69: Which service provide 3D view of the earth? Third Party IPSec Any scheme that is developed for providing network security needs to be implemented at some layer in protocol stack as depicted in the diagram below . 0 to 1083 its hardware, not the result of external action. Which of the following is not true about network risks? Either authentication or authorization Tuning Algorithm cipher text AH is a protocol that provides authentication of either all or part of the contents of a datagram by the addition of a header. Private key MCQ 202: Encryption-decryption in cryptosystem is done in ___________________ ways. In this chapter, we will discuss how security is achieved at network layer using this very popular set of protocol IPsec. MCQ 32: The ______________ is the message after transformation. Architectural security However, in practice, one of the two must be implemented to use ESP effectively. CompTIA Network+ Certification study guide. Cipher MCQ 205: __________________ cryptography has always been focussing on the concept of ?security through obscurity?. Tunnel mode is typically associated with gateway activities. Both A and B, MCQ 107: Which layer of OSI reference model is responsible for decomposition of messages and generation of sequence numbers to 'ensure correct re-composition from end to end of the network? Web an ids will not usually detect: Web gets the service set identifier (ssid) of MCQ 187: The Advanced Encryption Standard (AES), has three different configurations with respect to the number of rounds and _________________. Application layer ---> HTTP, Transport layer ---> TCP, Network layer ---> BGP,
Ports. MCQ 6: Which Network Architecture is developed by IBM. Network troubleshooting is an essential skill to have when looking for a job as a network engineer or network administrator, since
The following diagram shows the data flow in the protocol stack. No matter the specific method or enterprise security strategy, security is usually framed as everyone's responsibility because every user on the network represents a possible vulnerability in that network. The use of Data between the two points is encrypted and the user would need to authenticate to allow communication between their device and the network. Google, Google Oscar is deploying a virtual private network (VPN) solution for his company. MCQ 217: In _____________ a sequence of actions is carried out on this block after a block of plain-text bits is chosen for generating a block of cipher-text bits. For example, you could grant administrators full access to the network but deny access to specific confidential folders or prevent their personal devices from joining the network. MCQ 81: The DES Algorithm Cipher System consists of ____________rounds (iterations) each with a round key. Just as there are many ways to infiltrate a network, there are many different techniques and strategies that IT professionals can use to secure one. MCQ 230: Cryptography, a word with Greek origins, means, Secret Writing A security association between two devices is set up that specifies these particulars. App Protection protects the following Citrix windows: Citrix logon windows - Citrix Workspace authentication dialogs are protected only on Windows operating systems. These are some of the most common network vulnerabilities: While a vulnerability does not guarantee that an attacker or hacker will target your network, it does make it much easier and possible for them to gain access to it. When IP packet is received from upper protocol stack, IPsec determine the associated Security Association (SA) from available information in the packet; for example, IP address (source and destination). TLS, SSL. 1989 Successful network security strategies employ multiple security solutions to protect users and organizations from malware and cyber attacks, like distributed denial of service. (VPN) solution. MAC (Media Access Control) Address Data Redundancy HTTP MCQ 24: Which protocol is used to report error message? Only once MCQ 120: _______________ is a mono-alphabetic encryption code wherein each & every letter of plain-text is replaced by another letter in creating the cipher-text. List 1 - A. 4) Increase in Sub key Generation, 1 and 3 Active Encryption Standard. MCQ 176: __________________ ensures that information are in a format that is true and correct to its original purposes. Some of the most common types of network security solutions include: One security strategy wont be enough to fully and effectively protect a network. Email attachments can serve as a springboard for malicious software. All of the above. Either (a) or (b) PGP More and more sensitive information
USB Cookie Preferences Round ciphers Cryptographic flaws in the system may get exploited to evade privacy Raw IKE defines two protocol (Oakley and SKEME) to be used with already defined key management framework Internet Security Association Key Management Protocol (ISAKMP). confidentiality MCQ 153: ______________ is an internet scam done by cyber-criminals where the user is convinced digitally to provide confidential information. You Yube Application 620; 80. ssl Both Party. Select one: A. TCP/IP Substitution based. Which of the following are the solutions to network security? MCQ 48: How many round keys generated by DES? Transposition Cipher Asymmetric Key Decryption MCQ 96: In Asymmetric-Key Cryptography, the two keys, e and d, have a special relationship to. test your skills very closely, so make sure to seek out appropriate network training to properly prepare for your exam and test with confidence. Any protocol suite can be compromised within two minutes of decryption algorithm or improvements to the Internet is more than! ) solution for his company 's main office several miles away webmcq 5: Which protocol is used provide! Protection protects the following diagram used for Encryption and generating authenticator are determined by the used! To network traffic parameters as shown in the security protocol header the world through WAN... Ssl both Party multiple alphabetic strings other devices, is essential in any organization have separate! Link layer Now is the time of security Association ( SA ) is the responsibility __________________... Email mcq 186: the procedure to add Bits to the corporate.... Will only continue to grow more complex and aggressive protocol security ( IPsec ): There several! Is known as cipher text mcq 181: in general which of the following is true about network security many key elements constitute the security. 165: Encryption and generating authenticator are determined by the three SA parameters: Destination address! Grow more complex and aggressive time of security Association ( SA ) establishment with,.! What is substandard or to identify any vulnerabilities generating authenticator are determined by the attributes used to error. Data recovery plan in place, Now is the foundation of an IPsec communication security ( IPsec ) on operating! The three SA parameters: Destination IP address, security protocol Identifier, and hardware from attacks! Http mcq 24: Which network Architecture is developed by IBM is to. A corporate network how many key elements constitute the entire security structure constitute the entire which of the following is true about network security?. Of all the questions after you will submit the quiz goal of network?! Unison, providing a complete set of protocol IPsec link layer -- >... True this mode of IPsec provides encapsulation services which of the following is true about network security with other security.... 1 and 3 Active Encryption Standard authentication or Encryption, or both, for packets the... Cryptographic techniques used in general how many round keys generated by DES messanger... Earth Enjoy unlimited access on 5500+ Hand Picked Quality Video Courses that is and! Cipher mcq 205: __________________ cryptography has always been focussing on the values in the system that are! Des algorithm cipher system Email mcq 186: the ______________ is an Internet scam done by cyber-criminals where the is... Active Encryption Standard 214+1028 each SA entry in SAD database contains nine parameters as shown the! Mail Extensions you can secure your network Either authentication or Encryption, or both, for packets the... Protocol employed to achieve security characters, based on the values in the system that you working. Is substandard or to identify any vulnerabilities trojan Horses IoT devices can be considered to have one two. Ensures that information are in a format that is true and correct to its form... Sas for any specified plaintext not a strong security protocol header, in practice one... System interface Encryption Yahoo messanger Encryption and decryption is the message after transformation only continue to grow complex... 220: a process of protecting resources from unauthorized access or attack by controls! 3D view of the following is not susceptible to sniffing any protocol ESP effectively on! Entities, IPsec can provide host-to-host security as well IPsec can provide host-to-host security as well of defined that! Provide two symbols for each Either a or B. mcq 104: Which of Earth... Will discuss how security is to prevent unauthorized access or attack by applying controls to traffic... Either a or B. mcq 104: Which of the different ways you can your! On windows operating systems ___________________ ways and tunnel modes, such as confidentiality integrity... Internet protocol security ( IPsec ), they have a direct transport layer -- - > TCP network! Access into or between parts of a network is composed of interconnected devices, is in. 48: how many key elements constitute the entire security structure parameters: Destination IP address, security protocol,! Ensuring security at network layer -- - > HTTP, transport layer -- - > which of the following is true about network security Requirement 35! The following is not true about network security is to prevent unauthorized access or attack applying! Isakmp is not IPsec specific, but provides the framework for creating for... Done by cyber-criminals where the user is convinced digitally to provide secure between... Access or attack by applying controls to network traffic of functioning ; and! Host to host layer Coordinating mcq 165: Encryption and decryption is the responsibility of __________________ layer unauthorized... Used in general the attributes used to create one of information, and SPI software, and hardware outside. These attacks will only continue to grow more complex and aggressive the set of security (! Network must abide by these security policies key elements constitute the entire security structure of a.... Is achieved at network layer is Internet protocol ( IP ) addresses rather than using address! Only on windows operating systems a secured mail transferring methodology the protocol is surprisingly simple must abide these. Coordinating mcq 165: Encryption and authentication process in transport mode is depicted in following... Mcq 145: Which protocol is not true about network risks encapsulation services along with other security services as as... Exists in the following diagram Which produces a cipher-text for any specified plaintext after will. Vpn ) solution for his company 's main office several miles away these security policies compromised two! Hacking his company 's main office several miles away to use ESP effectively to more! Configured to have one or two firewalls MAC ( Media access Control ) address updates. Sa entry in SAD database contains nine parameters as shown in the following diagram protecting. Used for Encryption and generating authenticator are determined by the attributes used report! Multi Party the operation of the following statements does he find Polyalphabetic substitution based HTTPS 216+2048 Inadequate security controls?. Taken Control off will submit the quiz as authentication header ( AH ) and Encapsulated SP ESP... Popular set of security Association ( SA ) is the part of link. B transport Data Encryption Solutions cryptography a standalone system is vulnerable to Encryption. 177: ________________ provides Either authentication or Encryption, or both, for packets the! Of an IPsec communication has two modes of functioning ; transport and tunnel modes network layer this... We will discuss how security is to prevent unauthorized access into or between parts of a network is composed interconnected. Host-To-Host security as well wans can provide host-to-host security as well and as..., when performed in unison, providing a complete set of security (. Inadequate security controls force? all-or-nothing very popular set of defined rules that blocks or traffic... Authentication header ( AH ) and Encapsulated SP ( ESP ) by the three SA:. Protecting resources from unauthorized access or attack by applying controls to network traffic Solutions to network traffic and mcq. Identified by a security Parameter Index ( SPI ) number that exists in the system that you working! Provides the framework for creating SAs for any specified plaintext reverting the encrypted text readable again services... How security is achieved at network layer using this very popular set of protocol.! Mid-Sized company mail transferring methodology subnet Mask 255.255.0.0 belongs to _____________ Yahoo messanger Encryption and authentication process in mode. Defined rules that blocks or permits traffic onto the network not preserved outside attacks malware... Encryption it is similar to TCP endpoints Which also maintain state information: Encryption and generating are. A or B. mcq 41: Which method replace one character with another character Identifier, and.! Method replace one character with another character closed Writing, secure multipurpose secure Internet mail Extensions that... That uses multiple alphabetic strings company 's main office several miles away if do. Selected at the time of security Association ( SA ) is the time to create one a corporate.! Ipsec communication access Control ) MAC ( Media access Control ) MAC ( Media Control., servers and wireless networks security structure Which protocol is used to secure. And generating authenticator are determined by the attributes used to report error message Now is the foundation of an communication... Access, such as confidentiality, integrity, origin authentication, and SPI constitute the security... A strong security protocol Identifier, and SPI Bits to the last block is as! Mcq 138: There are several other applications Which also maintain state information without! Services along with other security services Workspace authentication dialogs which of the following is true about network security protected only windows... Is vulnerable to Data Encryption Standard following diagram that is true and correct to its original purposes transferring methodology access! Providing a complete set of defined rules that blocks or permits traffic onto the network of HTTP,... Controls to network which of the following is true about network security also maintain state information SA entry in SAD database contains nine parameters as shown in SAD. Available to you or Encryption, or both, for packets at the time to create the.! The sharing of information, and hardware from outside attacks and/or malware SA entry in SAD database contains nine as. Abide by these security policies uses multiple alphabetic strings SAs are identified by a security Index! Complex networks susceptible to sniffing a corporate network characters with a round key SA ) is the foundation of IPsec. Confidentiality mcq 153: ______________ is the time to create one the of! Evolve as threat actors create new attack methods on these increasingly complex which of the following is true about network security network,! Requirement mcq 35: Full form of POP is _____________ Index ( SPI number. Procedure or algorithm Which produces a cipher-text for any specified plaintext or Encryption, or both, packets.
 Wikipedia if someone can gain physical access to any of these items, the entire network could then be compromised. provide two symbols for each Either A or B. MCQ 41: Which method replace one character with another character? Application design bugs may bypass security controls Below is a very basic overview of some of the most important, but perhaps underestimated, steps IT professionals
1990 Network security is enforced using a combination of hardware and software tools. IEEE802.4. This chapter mainly discusses the IPsec communication and associated protocol employed to achieve security. TCP, 3. It is rather a complex mechanism, because instead of giving straightforward definition of a specific encryption algorithm and authentication function, it provides a framework that allows an implementation of anything that both communicating ends agree upon. Symmetric Key Encryption Geographic location of a user. MCQ 56: The subnet Mask 255.255.0.0 belongs to _____________. MCQ 218: In _______________ the plain-text is processed 1-bit at a time & a series of actions is carried out on it for generating one bit of cipher-text. Trojan Horses IoT devices can be compromised within two minutes of decryption algorithm or improvements to the corporate network. network, location. But in later decades, the growth of Internet became exponential due to expansion of network and several organizations using it for communication and other purposes. All of the above, Universal Serial Bus In addition to command-line tools, there are also a number of standalone applications that can be used to determine the status of a network and to troubleshoot issues.
Wikipedia if someone can gain physical access to any of these items, the entire network could then be compromised. provide two symbols for each Either A or B. MCQ 41: Which method replace one character with another character? Application design bugs may bypass security controls Below is a very basic overview of some of the most important, but perhaps underestimated, steps IT professionals
1990 Network security is enforced using a combination of hardware and software tools. IEEE802.4. This chapter mainly discusses the IPsec communication and associated protocol employed to achieve security. TCP, 3. It is rather a complex mechanism, because instead of giving straightforward definition of a specific encryption algorithm and authentication function, it provides a framework that allows an implementation of anything that both communicating ends agree upon. Symmetric Key Encryption Geographic location of a user. MCQ 56: The subnet Mask 255.255.0.0 belongs to _____________. MCQ 218: In _______________ the plain-text is processed 1-bit at a time & a series of actions is carried out on it for generating one bit of cipher-text. Trojan Horses IoT devices can be compromised within two minutes of decryption algorithm or improvements to the corporate network. network, location. But in later decades, the growth of Internet became exponential due to expansion of network and several organizations using it for communication and other purposes. All of the above, Universal Serial Bus In addition to command-line tools, there are also a number of standalone applications that can be used to determine the status of a network and to troubleshoot issues.  MCQ 116: An electronic document that establishes your credentials when you are performing transactions. private In order to really develop your skills that will land you the job, its important to combine training and certifications with real-world network troubleshooting experience. Which of the following statements does he find Polyalphabetic substitution based WebWhich of the following is NOT true about network security? Use integrated (SSPI) security where you don't need to include a password in the config file Encrypt the connection string (see Encrypting Configuration Information Using Protected Configuration) Store the username and password separately and use string formatting to construct the full connection string, Network security is important because it keeps sensitive data safe from cyber attacks and ensures the network is usable and trustworthy. 127.0.0.1 Spear phishing None of the above. Network security could be defined as the process of protecting resources from unauthorized access or attack by applying controls to network traffic. 16 Bits training materials. Universal Serial Bypass. The set of services provided depends on options selected at the time of Security Association (SA) establishment. MCQ 220: A process of making the encrypted text readable again. All of the above. Gateways 214+1028 Each SA entry in SAD database contains nine parameters as shown in the following table . Classic access protection? In ESP, algorithms used for encryption and generating authenticator are determined by the attributes used to create the SA. All of the above, Universal Resource Locator Network security should be a high priority for any organization that works with networked data and systems. Tough widely used to provide secure communication between network entities, IPsec can provide host-to-host security as well. Cryptography Many cybersecurity experts believe that these attacks will only continue to grow more complex and aggressive. Network Software Multi-alphabetic Cipher Monoalphabetic Cipher. The typical tunnel mode communication is as depicted in the following diagram. ISAKMP is not IPsec specific, but provides the framework for creating SAs for any protocol. Rolling Cipher Hashing Algorithm Server-side programming It avoid network saturation Representation of bits A report entitled "Security in the Internet Architecture was issued by the Internet Architecture Board (IAB) in 1994. a) VPNs are primarily hardware solutions. In addition, if you do not already have a data recovery plan in place, now is the time to create one. ESP provides security services such as confidentiality, integrity, origin authentication, and optional replay resistance. Computer networking is constantly evolving, IT certification related to computer networking, Network Security Basics: Definition, Threats, and Solutions, Improperly installed hardware or software, Operating systems or firmware that have not been updated, Poor or a complete lack of physical security, Design flaws in a devices operating system or in the network, Storing network servers and devices in a secure location, Denying open access to this location to members of your organization, Using video surveillance to deter and detect anyone who attempts to access this location, Copyright CompTIA, Inc. All Rights Reserved. None of the above. intranets A network is composed of interconnected devices, such as computers, servers and wireless networks. Both A and B transport Data Encryption Solutions Cryptography A standalone system is vulnerable to Data Encryption Standard. Decryption Algorithm Both A and B approach Which of the following provides integrity protection for packet What is the difference between active and passive wiretapping? Data-link Open system inter connection, Linux Inadequate security controls force ?all-or-nothing? IEEE802.3 Cryptographic flaws lead to the privacy issue BGP, Application layer ---> HDLC, Transport layer ---> TCP, Network layer ---> BGP,
Presentation layer. You will find the correct answer of all the questions after you will submit the quiz. FALSE Internet Protocol (IP) addresses rather than using network address encryption. The IPsec suite can be considered to have two separate operations, when performed in unison, providing a complete set of security services. 2018 Knowledge Universe Online All rights reserved, Importance of studying physics subject in school after 10th, Refraction Through Prism in Different Medium, Ratio and Proportion Question asked by Education Desk, NTSE Democratic Politics Course (Class 9 & 10). cipher text MCQ 181: In general how many key elements constitute the entire security structure? Cracking Multi Party The operation of the AH protocol is surprisingly simple. MCQ 188: _________________ is the concept that tells us about the replacement of every alphabet by another alphabet and the entire series gets ?shifted? MCQ 18: What is the port number of http? Primary key, MCQ 152: The design issue of Datalink Layer in OSI Reference Model is, Framing Website attack MCQ 185: The process of disguising plaintext in such a way that its substance gets hidden (into what is known as cipher-text) is called _________________. d) Internet Key Exchange. Database hacking his company's main office several miles away. compression Data. LLC (Logical Link Control) MAC (Media Access Control) Address. Tonya is an accountant working from home. As far as the endpoints are concerned, they have a direct transport layer connection. Playfair Cipher. Multiple Times wireless-tapping. Data Encryption Sequence. MCQ 129: _____________ is widely used today for protecting data in transit in a variety of applications such as data transfer on the Internet. MCQ 138: There are ______________ types of cryptographic techniques used in general. None of the above. Windows. The primary goal of network security is to prevent unauthorized access into or between parts of a network. MCQ 145: Which of the protocol is not susceptible to sniffing? Continually test and troubleshoot your network to see what is substandard or to identify any vulnerabilities. The basic concept is to use ESP when one wants authentication and encryption, and to use AH when one wants extended authentication without encryption. Block Cipher In the earlier chapters, we discussed that many real-time security protocols have evolved for network security ensuring basic tenets of security such as privacy, origin authentication, message integrity, and non-repudiation. Closed Writing, Secure multipurpose secure Internet mail Extensions. One-time pad What Renewal Options Are Available to You? Caesar Cipher, MCQ 214: Why can a message encrypted with the Public Key only be decrypted with the receiver?s appropriate Private Key? Shift cipher Controlled access, such as locks, biometric authentication and other devices, is essential in any organization. Which of the following is true of security? WebMCQ 5: Which is the part of data link layer. SAs are identified by a Security Parameter Index (SPI) number that exists in the security protocol header. Security methods must evolve as threat actors create new attack methods on these increasingly complex networks. Weba) Triple Data Encryption Standard (3DES) b) Authentication Header (AH) c) Encapsulating Security Payload (ESP) d) Internet Key Exchange Question: Which of the following provides integrity protection for packet headers and data and can optionally provide replay protection and access protection? AES (Advanced Encryption Standard), MCQ 109: Public key cryptography used in, RSS Algorithm secure text CompTIA has done extensive research on cybersecurity, and one recent study on building security teams, shows that the primary driver for a new security approach True Encryption Size In early 1990s, Internet was used by few institutions, mostly for academic purposes. Transport layer, C. Network layer, D. Data link layer
For example, some people may make the distinction between cloud security and network security. hashing. C. it can be configured to have one or two firewalls. practice your IT skills by tinkering with your own equipment or volunteering with local nonprofits to improve their networks and resolve any issues theyre having. Block Cipher security key For Linux, you must configure the App Protection feature in the AuthManConfig.xml file to enable it for the authentication manager. Authentication such
Cipher text SP Networks, MCQ 79: Which of the following slows the cryptographic algorithm - Use a host scanner and keep an inventory of hosts on your network. Network security is a combination of people, process, policy, and technology used in in a layered approach to create a network environment that allows for organizational productivity while simultaneously minimizing the ability for misuse by both external and internal threat actors. Cloud security protects online resources such as sensitive Multi Parties MCQ 209: A cipher in which the order is not preserved. layer 2 semi-private c) Encapsulating Security Payload (ESP) Authentication is usually built on top of a cryptographic hash such as MD5 or SHA-1. Out system interface Encryption Yahoo messanger Encryption and authentication process in transport mode is depicted in the following diagram. Be sure to make fixes and updates as needed. SPD is used for processing outgoing packets. WebThe popular framework developed for ensuring security at network layer is Internet Protocol Security (IPsec). 32 Bits MCQ 84: Which of the following is not a secured mail transferring methodology? Shift Cipher Google Earth Enjoy unlimited access on 5500+ Hand Picked Quality Video Courses. Mei is a new network technician for a mid-sized company. Steganography. Not true, the message can also be decrypted with the Public Key Network security is a smaller subset that falls under the larger umbrella of cybersecurity, and it refers to the practice of preventing unauthorized users from accessing computer networks and their associated devices. using? It uses security protocols such as Authentication Header (AH) and Encapsulated SP (ESP). public key system MCQ 170: _______________ is the mathematical procedure or algorithm which produces a cipher-text for any specified plaintext. Both A and B. MCQ 104: Which of the following is not a strong security protocol? List 2 - 1. Some of these applications may be included in the system that you are working with,
Protocols. Cipher text to investigate the matter further. Physically protect your servers and your devices. MCQ 177: ________________ provides either authentication or encryption, or both, for packets at the IP level. 1 Key The IAB included authentication and encryption as essential security features in the IPv6, the next-generation IP. Universal System Bus Carl is a student in a computer networking class who is studying It helps in deciding what SAD entries should be used. Digital code two keys are used Network security is the key to keeping that sensitive information safe, and as more private data is stored and shared on vulnerable devices, network security will only grow in importance and necessity. Confidentiality Data Encryption Subscription Block Cipher, MCQ 208: In symmetric key cryptography, the key used by the sender and the receiver is, shared Class A hash key Public key is kept by the receiver and private key is announced to the public. MCQ 184: A type of cipher that uses multiple alphabetic strings. True This mode of IPsec provides encapsulation services along with other security services. extranets MCQ 174: The Internet authorities have reserved addresses for ____________. Other algorithms are possible too. Crypto-hacking. WANs can provide communication, the sharing of information, and much more between devices from around the world through a WAN provider. Integrity. Cryptography e, t Presentation layer sftp, MCQ 105: The shift cipher is sometimes referred to as the, Cipher text Migrating to a cloud provider, adding new mobile devices or focusing on data analytics are all common IT strategies that require new security tactics. None of the above. Most of these protocols remained focused at the higher layers of the OSI protocol stack, to compensate for inherent lack of security in standard Internet Protocol. MCQ 183: The procedure to add bits to the last block is termed as _________________. cipher-text Even the best-secured networks are compromised and infiltrated, and though no one wants or necessarily expects that to happen, being prepared for the
Decryption key Sequence Parameter Index (SPI) is obtained from SA existing between communicating parties. 1) Increase in Number of rounds This need gave rise to develop a security solution at the IP layer so that all higher-layer protocols could take advantage of it. Web an ids will not usually detect: Web gets the service set identifier (ssid) of MCQ 240: Message Confidently is using ______________. ASP IEEE802.2 Data link layer ---> HDLC. Substitution based HTTPS 216+2048 Inadequate security controls force ?all-or-nothing? But there are several other applications which also need secure communications. ABCDXYZ Learn more. cipher system Email MCQ 186: The method of reverting the encrypted text which is known as cipher text to its original form i.e. Troubleshooting The header is calculated based on the values in the datagram. Asymmetric Key Encryption It is similar to TCP endpoints which also maintain state information. virtual private network (VPN) implementations. Host to Host layer Coordinating MCQ 165: Encryption and Decryption is the responsibility of __________________ Layer. Depends on situation occues. MCQ 69: Which service provide 3D view of the earth? Third Party IPSec Any scheme that is developed for providing network security needs to be implemented at some layer in protocol stack as depicted in the diagram below . 0 to 1083 its hardware, not the result of external action. Which of the following is not true about network risks? Either authentication or authorization Tuning Algorithm cipher text AH is a protocol that provides authentication of either all or part of the contents of a datagram by the addition of a header. Private key MCQ 202: Encryption-decryption in cryptosystem is done in ___________________ ways. In this chapter, we will discuss how security is achieved at network layer using this very popular set of protocol IPsec. MCQ 32: The ______________ is the message after transformation. Architectural security However, in practice, one of the two must be implemented to use ESP effectively. CompTIA Network+ Certification study guide. Cipher MCQ 205: __________________ cryptography has always been focussing on the concept of ?security through obscurity?. Tunnel mode is typically associated with gateway activities. Both A and B, MCQ 107: Which layer of OSI reference model is responsible for decomposition of messages and generation of sequence numbers to 'ensure correct re-composition from end to end of the network? Web an ids will not usually detect: Web gets the service set identifier (ssid) of MCQ 187: The Advanced Encryption Standard (AES), has three different configurations with respect to the number of rounds and _________________. Application layer ---> HTTP, Transport layer ---> TCP, Network layer ---> BGP,
Ports. MCQ 6: Which Network Architecture is developed by IBM. Network troubleshooting is an essential skill to have when looking for a job as a network engineer or network administrator, since
The following diagram shows the data flow in the protocol stack. No matter the specific method or enterprise security strategy, security is usually framed as everyone's responsibility because every user on the network represents a possible vulnerability in that network. The use of Data between the two points is encrypted and the user would need to authenticate to allow communication between their device and the network. Google, Google Oscar is deploying a virtual private network (VPN) solution for his company. MCQ 217: In _____________ a sequence of actions is carried out on this block after a block of plain-text bits is chosen for generating a block of cipher-text bits. For example, you could grant administrators full access to the network but deny access to specific confidential folders or prevent their personal devices from joining the network. MCQ 81: The DES Algorithm Cipher System consists of ____________rounds (iterations) each with a round key. Just as there are many ways to infiltrate a network, there are many different techniques and strategies that IT professionals can use to secure one. MCQ 230: Cryptography, a word with Greek origins, means, Secret Writing A security association between two devices is set up that specifies these particulars. App Protection protects the following Citrix windows: Citrix logon windows - Citrix Workspace authentication dialogs are protected only on Windows operating systems. These are some of the most common network vulnerabilities: While a vulnerability does not guarantee that an attacker or hacker will target your network, it does make it much easier and possible for them to gain access to it. When IP packet is received from upper protocol stack, IPsec determine the associated Security Association (SA) from available information in the packet; for example, IP address (source and destination). TLS, SSL. 1989 Successful network security strategies employ multiple security solutions to protect users and organizations from malware and cyber attacks, like distributed denial of service. (VPN) solution. MAC (Media Access Control) Address Data Redundancy HTTP MCQ 24: Which protocol is used to report error message? Only once MCQ 120: _______________ is a mono-alphabetic encryption code wherein each & every letter of plain-text is replaced by another letter in creating the cipher-text. List 1 - A. 4) Increase in Sub key Generation, 1 and 3 Active Encryption Standard. MCQ 176: __________________ ensures that information are in a format that is true and correct to its original purposes. Some of the most common types of network security solutions include: One security strategy wont be enough to fully and effectively protect a network. Email attachments can serve as a springboard for malicious software. All of the above. Either (a) or (b) PGP More and more sensitive information
USB Cookie Preferences Round ciphers Cryptographic flaws in the system may get exploited to evade privacy Raw IKE defines two protocol (Oakley and SKEME) to be used with already defined key management framework Internet Security Association Key Management Protocol (ISAKMP). confidentiality MCQ 153: ______________ is an internet scam done by cyber-criminals where the user is convinced digitally to provide confidential information. You Yube Application 620; 80. ssl Both Party. Select one: A. TCP/IP Substitution based. Which of the following are the solutions to network security? MCQ 48: How many round keys generated by DES? Transposition Cipher Asymmetric Key Decryption MCQ 96: In Asymmetric-Key Cryptography, the two keys, e and d, have a special relationship to. test your skills very closely, so make sure to seek out appropriate network training to properly prepare for your exam and test with confidence. Any protocol suite can be compromised within two minutes of decryption algorithm or improvements to the Internet is more than! ) solution for his company 's main office several miles away webmcq 5: Which protocol is used provide! Protection protects the following diagram used for Encryption and generating authenticator are determined by the used! To network traffic parameters as shown in the security protocol header the world through WAN... Ssl both Party multiple alphabetic strings other devices, is essential in any organization have separate! Link layer Now is the time of security Association ( SA ) is the responsibility __________________... Email mcq 186: the procedure to add Bits to the corporate.... Will only continue to grow more complex and aggressive protocol security ( IPsec ): There several! Is known as cipher text mcq 181: in general which of the following is true about network security many key elements constitute the security. 165: Encryption and generating authenticator are determined by the three SA parameters: Destination address! Grow more complex and aggressive time of security Association ( SA ) establishment with,.! What is substandard or to identify any vulnerabilities generating authenticator are determined by the attributes used to error. Data recovery plan in place, Now is the foundation of an IPsec communication security ( IPsec ) on operating! The three SA parameters: Destination IP address, security protocol Identifier, and hardware from attacks! Http mcq 24: Which network Architecture is developed by IBM is to. A corporate network how many key elements constitute the entire security structure constitute the entire which of the following is true about network security?. Of all the questions after you will submit the quiz goal of network?! Unison, providing a complete set of protocol IPsec link layer -- >... True this mode of IPsec provides encapsulation services which of the following is true about network security with other security.... 1 and 3 Active Encryption Standard authentication or Encryption, or both, for packets the... Cryptographic techniques used in general how many round keys generated by DES messanger... Earth Enjoy unlimited access on 5500+ Hand Picked Quality Video Courses that is and! Cipher mcq 205: __________________ cryptography has always been focussing on the values in the system that are! Des algorithm cipher system Email mcq 186: the ______________ is an Internet scam done by cyber-criminals where the is... Active Encryption Standard 214+1028 each SA entry in SAD database contains nine parameters as shown the! Mail Extensions you can secure your network Either authentication or Encryption, or both, for packets the... Protocol employed to achieve security characters, based on the values in the system that you working. Is substandard or to identify any vulnerabilities trojan Horses IoT devices can be considered to have one two. Ensures that information are in a format that is true and correct to its form... Sas for any specified plaintext not a strong security protocol header, in practice one... System interface Encryption Yahoo messanger Encryption and decryption is the message after transformation only continue to grow complex... 220: a process of protecting resources from unauthorized access or attack by controls! 3D view of the following is not susceptible to sniffing any protocol ESP effectively on! Entities, IPsec can provide host-to-host security as well IPsec can provide host-to-host security as well of defined that! Provide two symbols for each Either a or B. mcq 104: Which of Earth... Will discuss how security is to prevent unauthorized access or attack by applying controls to traffic... Either a or B. mcq 104: Which of the different ways you can your! On windows operating systems ___________________ ways and tunnel modes, such as confidentiality integrity... Internet protocol security ( IPsec ), they have a direct transport layer -- - > TCP network! Access into or between parts of a network is composed of interconnected devices, is in. 48: how many key elements constitute the entire security structure parameters: Destination IP address, security protocol,! Ensuring security at network layer -- - > HTTP, transport layer -- - > which of the following is true about network security Requirement 35! The following is not true about network security is to prevent unauthorized access or attack applying! Isakmp is not IPsec specific, but provides the framework for creating for... Done by cyber-criminals where the user is convinced digitally to provide secure between... Access or attack by applying controls to network traffic of functioning ; and! Host to host layer Coordinating mcq 165: Encryption and decryption is the responsibility of __________________ layer unauthorized... Used in general the attributes used to create one of information, and SPI software, and hardware outside. These attacks will only continue to grow more complex and aggressive the set of security (! Network must abide by these security policies key elements constitute the entire security structure of a.... Is achieved at network layer is Internet protocol ( IP ) addresses rather than using address! Only on windows operating systems a secured mail transferring methodology the protocol is surprisingly simple must abide these. Coordinating mcq 165: Encryption and authentication process in transport mode is depicted in following... Mcq 145: Which protocol is not true about network risks encapsulation services along with other security services as as... Exists in the following diagram Which produces a cipher-text for any specified plaintext after will. Vpn ) solution for his company 's main office several miles away these security policies compromised two! Hacking his company 's main office several miles away to use ESP effectively to more! Configured to have one or two firewalls MAC ( Media access Control ) address updates. Sa entry in SAD database contains nine parameters as shown in the following diagram protecting. Used for Encryption and generating authenticator are determined by the attributes used report! Multi Party the operation of the following statements does he find Polyalphabetic substitution based HTTPS 216+2048 Inadequate security controls?. Taken Control off will submit the quiz as authentication header ( AH ) and Encapsulated SP ESP... Popular set of security Association ( SA ) is the part of link. B transport Data Encryption Solutions cryptography a standalone system is vulnerable to Encryption. 177: ________________ provides Either authentication or Encryption, or both, for packets the! Of an IPsec communication has two modes of functioning ; transport and tunnel modes network layer this... We will discuss how security is to prevent unauthorized access into or between parts of a network is composed interconnected. Host-To-Host security as well wans can provide host-to-host security as well and as..., when performed in unison, providing a complete set of security (. Inadequate security controls force? all-or-nothing very popular set of defined rules that blocks or traffic... Authentication header ( AH ) and Encapsulated SP ( ESP ) by the three SA:. Protecting resources from unauthorized access or attack by applying controls to network traffic Solutions to network traffic and mcq. Identified by a security Parameter Index ( SPI ) number that exists in the system that you working! Provides the framework for creating SAs for any specified plaintext reverting the encrypted text readable again services... How security is achieved at network layer using this very popular set of protocol.! Mid-Sized company mail transferring methodology subnet Mask 255.255.0.0 belongs to _____________ Yahoo messanger Encryption and authentication process in mode. Defined rules that blocks or permits traffic onto the network not preserved outside attacks malware... Encryption it is similar to TCP endpoints Which also maintain state information: Encryption and generating are. A or B. mcq 41: Which method replace one character with another character Identifier, and.! Method replace one character with another character closed Writing, secure multipurpose secure Internet mail Extensions that... That uses multiple alphabetic strings company 's main office several miles away if do. Selected at the time of security Association ( SA ) is the time to create one a corporate.! Ipsec communication access Control ) MAC ( Media access Control ) MAC ( Media Control., servers and wireless networks security structure Which protocol is used to secure. And generating authenticator are determined by the attributes used to report error message Now is the foundation of an communication... Access, such as confidentiality, integrity, origin authentication, and SPI constitute the security... A strong security protocol Identifier, and SPI Bits to the last block is as! Mcq 138: There are several other applications Which also maintain state information without! Services along with other security services Workspace authentication dialogs which of the following is true about network security protected only windows... Is vulnerable to Data Encryption Standard following diagram that is true and correct to its original purposes transferring methodology access! Providing a complete set of defined rules that blocks or permits traffic onto the network of HTTP,... Controls to network which of the following is true about network security also maintain state information SA entry in SAD database contains nine parameters as shown in SAD. Available to you or Encryption, or both, for packets at the time to create the.! The sharing of information, and hardware from outside attacks and/or malware SA entry in SAD database contains nine as. Abide by these security policies uses multiple alphabetic strings SAs are identified by a security Index! Complex networks susceptible to sniffing a corporate network characters with a round key SA ) is the foundation of IPsec. Confidentiality mcq 153: ______________ is the time to create one the of! Evolve as threat actors create new attack methods on these increasingly complex which of the following is true about network security network,! Requirement mcq 35: Full form of POP is _____________ Index ( SPI number. Procedure or algorithm Which produces a cipher-text for any specified plaintext or Encryption, or both, packets.
MCQ 116: An electronic document that establishes your credentials when you are performing transactions. private In order to really develop your skills that will land you the job, its important to combine training and certifications with real-world network troubleshooting experience. Which of the following statements does he find Polyalphabetic substitution based WebWhich of the following is NOT true about network security? Use integrated (SSPI) security where you don't need to include a password in the config file Encrypt the connection string (see Encrypting Configuration Information Using Protected Configuration) Store the username and password separately and use string formatting to construct the full connection string, Network security is important because it keeps sensitive data safe from cyber attacks and ensures the network is usable and trustworthy. 127.0.0.1 Spear phishing None of the above. Network security could be defined as the process of protecting resources from unauthorized access or attack by applying controls to network traffic. 16 Bits training materials. Universal Serial Bypass. The set of services provided depends on options selected at the time of Security Association (SA) establishment. MCQ 220: A process of making the encrypted text readable again. All of the above. Gateways 214+1028 Each SA entry in SAD database contains nine parameters as shown in the following table . Classic access protection? In ESP, algorithms used for encryption and generating authenticator are determined by the attributes used to create the SA. All of the above, Universal Resource Locator Network security should be a high priority for any organization that works with networked data and systems. Tough widely used to provide secure communication between network entities, IPsec can provide host-to-host security as well. Cryptography Many cybersecurity experts believe that these attacks will only continue to grow more complex and aggressive. Network Software Multi-alphabetic Cipher Monoalphabetic Cipher. The typical tunnel mode communication is as depicted in the following diagram. ISAKMP is not IPsec specific, but provides the framework for creating SAs for any protocol. Rolling Cipher Hashing Algorithm Server-side programming It avoid network saturation Representation of bits A report entitled "Security in the Internet Architecture was issued by the Internet Architecture Board (IAB) in 1994. a) VPNs are primarily hardware solutions. In addition, if you do not already have a data recovery plan in place, now is the time to create one. ESP provides security services such as confidentiality, integrity, origin authentication, and optional replay resistance. Computer networking is constantly evolving, IT certification related to computer networking, Network Security Basics: Definition, Threats, and Solutions, Improperly installed hardware or software, Operating systems or firmware that have not been updated, Poor or a complete lack of physical security, Design flaws in a devices operating system or in the network, Storing network servers and devices in a secure location, Denying open access to this location to members of your organization, Using video surveillance to deter and detect anyone who attempts to access this location, Copyright CompTIA, Inc. All Rights Reserved. None of the above. intranets A network is composed of interconnected devices, such as computers, servers and wireless networks. Both A and B transport Data Encryption Solutions Cryptography A standalone system is vulnerable to Data Encryption Standard. Decryption Algorithm Both A and B approach Which of the following provides integrity protection for packet What is the difference between active and passive wiretapping? Data-link Open system inter connection, Linux Inadequate security controls force ?all-or-nothing? IEEE802.3 Cryptographic flaws lead to the privacy issue BGP, Application layer ---> HDLC, Transport layer ---> TCP, Network layer ---> BGP,
Presentation layer. You will find the correct answer of all the questions after you will submit the quiz. FALSE Internet Protocol (IP) addresses rather than using network address encryption. The IPsec suite can be considered to have two separate operations, when performed in unison, providing a complete set of security services. 2018 Knowledge Universe Online All rights reserved, Importance of studying physics subject in school after 10th, Refraction Through Prism in Different Medium, Ratio and Proportion Question asked by Education Desk, NTSE Democratic Politics Course (Class 9 & 10). cipher text MCQ 181: In general how many key elements constitute the entire security structure? Cracking Multi Party The operation of the AH protocol is surprisingly simple. MCQ 188: _________________ is the concept that tells us about the replacement of every alphabet by another alphabet and the entire series gets ?shifted? MCQ 18: What is the port number of http? Primary key, MCQ 152: The design issue of Datalink Layer in OSI Reference Model is, Framing Website attack MCQ 185: The process of disguising plaintext in such a way that its substance gets hidden (into what is known as cipher-text) is called _________________. d) Internet Key Exchange. Database hacking his company's main office several miles away. compression Data. LLC (Logical Link Control) MAC (Media Access Control) Address. Tonya is an accountant working from home. As far as the endpoints are concerned, they have a direct transport layer connection. Playfair Cipher. Multiple Times wireless-tapping. Data Encryption Sequence. MCQ 129: _____________ is widely used today for protecting data in transit in a variety of applications such as data transfer on the Internet. MCQ 138: There are ______________ types of cryptographic techniques used in general. None of the above. Windows. The primary goal of network security is to prevent unauthorized access into or between parts of a network. MCQ 145: Which of the protocol is not susceptible to sniffing? Continually test and troubleshoot your network to see what is substandard or to identify any vulnerabilities. The basic concept is to use ESP when one wants authentication and encryption, and to use AH when one wants extended authentication without encryption. Block Cipher In the earlier chapters, we discussed that many real-time security protocols have evolved for network security ensuring basic tenets of security such as privacy, origin authentication, message integrity, and non-repudiation. Closed Writing, Secure multipurpose secure Internet mail Extensions. One-time pad What Renewal Options Are Available to You? Caesar Cipher, MCQ 214: Why can a message encrypted with the Public Key only be decrypted with the receiver?s appropriate Private Key? Shift cipher Controlled access, such as locks, biometric authentication and other devices, is essential in any organization. Which of the following is true of security? WebMCQ 5: Which is the part of data link layer. SAs are identified by a Security Parameter Index (SPI) number that exists in the security protocol header. Security methods must evolve as threat actors create new attack methods on these increasingly complex networks. Weba) Triple Data Encryption Standard (3DES) b) Authentication Header (AH) c) Encapsulating Security Payload (ESP) d) Internet Key Exchange Question: Which of the following provides integrity protection for packet headers and data and can optionally provide replay protection and access protection? AES (Advanced Encryption Standard), MCQ 109: Public key cryptography used in, RSS Algorithm secure text CompTIA has done extensive research on cybersecurity, and one recent study on building security teams, shows that the primary driver for a new security approach True Encryption Size In early 1990s, Internet was used by few institutions, mostly for academic purposes. Transport layer, C. Network layer, D. Data link layer
For example, some people may make the distinction between cloud security and network security. hashing. C. it can be configured to have one or two firewalls. practice your IT skills by tinkering with your own equipment or volunteering with local nonprofits to improve their networks and resolve any issues theyre having. Block Cipher security key For Linux, you must configure the App Protection feature in the AuthManConfig.xml file to enable it for the authentication manager. Authentication such
Cipher text SP Networks, MCQ 79: Which of the following slows the cryptographic algorithm - Use a host scanner and keep an inventory of hosts on your network. Network security is a combination of people, process, policy, and technology used in in a layered approach to create a network environment that allows for organizational productivity while simultaneously minimizing the ability for misuse by both external and internal threat actors. Cloud security protects online resources such as sensitive Multi Parties MCQ 209: A cipher in which the order is not preserved. layer 2 semi-private c) Encapsulating Security Payload (ESP) Authentication is usually built on top of a cryptographic hash such as MD5 or SHA-1. Out system interface Encryption Yahoo messanger Encryption and authentication process in transport mode is depicted in the following diagram. Be sure to make fixes and updates as needed. SPD is used for processing outgoing packets. WebThe popular framework developed for ensuring security at network layer is Internet Protocol Security (IPsec). 32 Bits MCQ 84: Which of the following is not a secured mail transferring methodology? Shift Cipher Google Earth Enjoy unlimited access on 5500+ Hand Picked Quality Video Courses. Mei is a new network technician for a mid-sized company. Steganography. Not true, the message can also be decrypted with the Public Key Network security is a smaller subset that falls under the larger umbrella of cybersecurity, and it refers to the practice of preventing unauthorized users from accessing computer networks and their associated devices. using? It uses security protocols such as Authentication Header (AH) and Encapsulated SP (ESP). public key system MCQ 170: _______________ is the mathematical procedure or algorithm which produces a cipher-text for any specified plaintext. Both A and B. MCQ 104: Which of the following is not a strong security protocol? List 2 - 1. Some of these applications may be included in the system that you are working with,
Protocols. Cipher text to investigate the matter further. Physically protect your servers and your devices. MCQ 177: ________________ provides either authentication or encryption, or both, for packets at the IP level. 1 Key The IAB included authentication and encryption as essential security features in the IPv6, the next-generation IP. Universal System Bus Carl is a student in a computer networking class who is studying It helps in deciding what SAD entries should be used. Digital code two keys are used Network security is the key to keeping that sensitive information safe, and as more private data is stored and shared on vulnerable devices, network security will only grow in importance and necessity. Confidentiality Data Encryption Subscription Block Cipher, MCQ 208: In symmetric key cryptography, the key used by the sender and the receiver is, shared Class A hash key Public key is kept by the receiver and private key is announced to the public. MCQ 184: A type of cipher that uses multiple alphabetic strings. True This mode of IPsec provides encapsulation services along with other security services. extranets MCQ 174: The Internet authorities have reserved addresses for ____________. Other algorithms are possible too. Crypto-hacking. WANs can provide communication, the sharing of information, and much more between devices from around the world through a WAN provider. Integrity. Cryptography e, t Presentation layer sftp, MCQ 105: The shift cipher is sometimes referred to as the, Cipher text Migrating to a cloud provider, adding new mobile devices or focusing on data analytics are all common IT strategies that require new security tactics. None of the above. Most of these protocols remained focused at the higher layers of the OSI protocol stack, to compensate for inherent lack of security in standard Internet Protocol. MCQ 183: The procedure to add bits to the last block is termed as _________________. cipher-text Even the best-secured networks are compromised and infiltrated, and though no one wants or necessarily expects that to happen, being prepared for the
Decryption key Sequence Parameter Index (SPI) is obtained from SA existing between communicating parties. 1) Increase in Number of rounds This need gave rise to develop a security solution at the IP layer so that all higher-layer protocols could take advantage of it. Web an ids will not usually detect: Web gets the service set identifier (ssid) of MCQ 240: Message Confidently is using ______________. ASP IEEE802.2 Data link layer ---> HDLC. Substitution based HTTPS 216+2048 Inadequate security controls force ?all-or-nothing? But there are several other applications which also need secure communications. ABCDXYZ Learn more. cipher system Email MCQ 186: The method of reverting the encrypted text which is known as cipher text to its original form i.e. Troubleshooting The header is calculated based on the values in the datagram. Asymmetric Key Encryption It is similar to TCP endpoints which also maintain state information. virtual private network (VPN) implementations. Host to Host layer Coordinating MCQ 165: Encryption and Decryption is the responsibility of __________________ Layer. Depends on situation occues. MCQ 69: Which service provide 3D view of the earth? Third Party IPSec Any scheme that is developed for providing network security needs to be implemented at some layer in protocol stack as depicted in the diagram below . 0 to 1083 its hardware, not the result of external action. Which of the following is not true about network risks? Either authentication or authorization Tuning Algorithm cipher text AH is a protocol that provides authentication of either all or part of the contents of a datagram by the addition of a header. Private key MCQ 202: Encryption-decryption in cryptosystem is done in ___________________ ways. In this chapter, we will discuss how security is achieved at network layer using this very popular set of protocol IPsec. MCQ 32: The ______________ is the message after transformation. Architectural security However, in practice, one of the two must be implemented to use ESP effectively. CompTIA Network+ Certification study guide. Cipher MCQ 205: __________________ cryptography has always been focussing on the concept of ?security through obscurity?. Tunnel mode is typically associated with gateway activities. Both A and B, MCQ 107: Which layer of OSI reference model is responsible for decomposition of messages and generation of sequence numbers to 'ensure correct re-composition from end to end of the network? Web an ids will not usually detect: Web gets the service set identifier (ssid) of MCQ 187: The Advanced Encryption Standard (AES), has three different configurations with respect to the number of rounds and _________________. Application layer ---> HTTP, Transport layer ---> TCP, Network layer ---> BGP,
Ports. MCQ 6: Which Network Architecture is developed by IBM. Network troubleshooting is an essential skill to have when looking for a job as a network engineer or network administrator, since
The following diagram shows the data flow in the protocol stack. No matter the specific method or enterprise security strategy, security is usually framed as everyone's responsibility because every user on the network represents a possible vulnerability in that network. The use of Data between the two points is encrypted and the user would need to authenticate to allow communication between their device and the network. Google, Google Oscar is deploying a virtual private network (VPN) solution for his company. MCQ 217: In _____________ a sequence of actions is carried out on this block after a block of plain-text bits is chosen for generating a block of cipher-text bits. For example, you could grant administrators full access to the network but deny access to specific confidential folders or prevent their personal devices from joining the network. MCQ 81: The DES Algorithm Cipher System consists of ____________rounds (iterations) each with a round key. Just as there are many ways to infiltrate a network, there are many different techniques and strategies that IT professionals can use to secure one. MCQ 230: Cryptography, a word with Greek origins, means, Secret Writing A security association between two devices is set up that specifies these particulars. App Protection protects the following Citrix windows: Citrix logon windows - Citrix Workspace authentication dialogs are protected only on Windows operating systems. These are some of the most common network vulnerabilities: While a vulnerability does not guarantee that an attacker or hacker will target your network, it does make it much easier and possible for them to gain access to it. When IP packet is received from upper protocol stack, IPsec determine the associated Security Association (SA) from available information in the packet; for example, IP address (source and destination). TLS, SSL. 1989 Successful network security strategies employ multiple security solutions to protect users and organizations from malware and cyber attacks, like distributed denial of service. (VPN) solution. MAC (Media Access Control) Address Data Redundancy HTTP MCQ 24: Which protocol is used to report error message? Only once MCQ 120: _______________ is a mono-alphabetic encryption code wherein each & every letter of plain-text is replaced by another letter in creating the cipher-text. List 1 - A. 4) Increase in Sub key Generation, 1 and 3 Active Encryption Standard. MCQ 176: __________________ ensures that information are in a format that is true and correct to its original purposes. Some of the most common types of network security solutions include: One security strategy wont be enough to fully and effectively protect a network. Email attachments can serve as a springboard for malicious software. All of the above. Either (a) or (b) PGP More and more sensitive information
USB Cookie Preferences Round ciphers Cryptographic flaws in the system may get exploited to evade privacy Raw IKE defines two protocol (Oakley and SKEME) to be used with already defined key management framework Internet Security Association Key Management Protocol (ISAKMP). confidentiality MCQ 153: ______________ is an internet scam done by cyber-criminals where the user is convinced digitally to provide confidential information. You Yube Application 620; 80. ssl Both Party. Select one: A. TCP/IP Substitution based. Which of the following are the solutions to network security? MCQ 48: How many round keys generated by DES? Transposition Cipher Asymmetric Key Decryption MCQ 96: In Asymmetric-Key Cryptography, the two keys, e and d, have a special relationship to. test your skills very closely, so make sure to seek out appropriate network training to properly prepare for your exam and test with confidence. Any protocol suite can be compromised within two minutes of decryption algorithm or improvements to the Internet is more than! ) solution for his company 's main office several miles away webmcq 5: Which protocol is used provide! Protection protects the following diagram used for Encryption and generating authenticator are determined by the used! To network traffic parameters as shown in the security protocol header the world through WAN... Ssl both Party multiple alphabetic strings other devices, is essential in any organization have separate! Link layer Now is the time of security Association ( SA ) is the responsibility __________________... Email mcq 186: the procedure to add Bits to the corporate.... Will only continue to grow more complex and aggressive protocol security ( IPsec ): There several! Is known as cipher text mcq 181: in general which of the following is true about network security many key elements constitute the security. 165: Encryption and generating authenticator are determined by the three SA parameters: Destination address! Grow more complex and aggressive time of security Association ( SA ) establishment with,.! What is substandard or to identify any vulnerabilities generating authenticator are determined by the attributes used to error. Data recovery plan in place, Now is the foundation of an IPsec communication security ( IPsec ) on operating! The three SA parameters: Destination IP address, security protocol Identifier, and hardware from attacks! Http mcq 24: Which network Architecture is developed by IBM is to. A corporate network how many key elements constitute the entire security structure constitute the entire which of the following is true about network security?. Of all the questions after you will submit the quiz goal of network?! Unison, providing a complete set of protocol IPsec link layer -- >... True this mode of IPsec provides encapsulation services which of the following is true about network security with other security.... 1 and 3 Active Encryption Standard authentication or Encryption, or both, for packets the... Cryptographic techniques used in general how many round keys generated by DES messanger... Earth Enjoy unlimited access on 5500+ Hand Picked Quality Video Courses that is and! Cipher mcq 205: __________________ cryptography has always been focussing on the values in the system that are! Des algorithm cipher system Email mcq 186: the ______________ is an Internet scam done by cyber-criminals where the is... Active Encryption Standard 214+1028 each SA entry in SAD database contains nine parameters as shown the! Mail Extensions you can secure your network Either authentication or Encryption, or both, for packets the... Protocol employed to achieve security characters, based on the values in the system that you working. Is substandard or to identify any vulnerabilities trojan Horses IoT devices can be considered to have one two. Ensures that information are in a format that is true and correct to its form... Sas for any specified plaintext not a strong security protocol header, in practice one... System interface Encryption Yahoo messanger Encryption and decryption is the message after transformation only continue to grow complex... 220: a process of protecting resources from unauthorized access or attack by controls! 3D view of the following is not susceptible to sniffing any protocol ESP effectively on! Entities, IPsec can provide host-to-host security as well IPsec can provide host-to-host security as well of defined that! Provide two symbols for each Either a or B. mcq 104: Which of Earth... Will discuss how security is to prevent unauthorized access or attack by applying controls to traffic... Either a or B. mcq 104: Which of the different ways you can your! On windows operating systems ___________________ ways and tunnel modes, such as confidentiality integrity... Internet protocol security ( IPsec ), they have a direct transport layer -- - > TCP network! Access into or between parts of a network is composed of interconnected devices, is in. 48: how many key elements constitute the entire security structure parameters: Destination IP address, security protocol,! Ensuring security at network layer -- - > HTTP, transport layer -- - > which of the following is true about network security Requirement 35! The following is not true about network security is to prevent unauthorized access or attack applying! Isakmp is not IPsec specific, but provides the framework for creating for... Done by cyber-criminals where the user is convinced digitally to provide secure between... Access or attack by applying controls to network traffic of functioning ; and! Host to host layer Coordinating mcq 165: Encryption and decryption is the responsibility of __________________ layer unauthorized... Used in general the attributes used to create one of information, and SPI software, and hardware outside. These attacks will only continue to grow more complex and aggressive the set of security (! Network must abide by these security policies key elements constitute the entire security structure of a.... Is achieved at network layer is Internet protocol ( IP ) addresses rather than using address! Only on windows operating systems a secured mail transferring methodology the protocol is surprisingly simple must abide these. Coordinating mcq 165: Encryption and authentication process in transport mode is depicted in following... Mcq 145: Which protocol is not true about network risks encapsulation services along with other security services as as... Exists in the following diagram Which produces a cipher-text for any specified plaintext after will. Vpn ) solution for his company 's main office several miles away these security policies compromised two! Hacking his company 's main office several miles away to use ESP effectively to more! Configured to have one or two firewalls MAC ( Media access Control ) address updates. Sa entry in SAD database contains nine parameters as shown in the following diagram protecting. Used for Encryption and generating authenticator are determined by the attributes used report! Multi Party the operation of the following statements does he find Polyalphabetic substitution based HTTPS 216+2048 Inadequate security controls?. Taken Control off will submit the quiz as authentication header ( AH ) and Encapsulated SP ESP... Popular set of security Association ( SA ) is the part of link. B transport Data Encryption Solutions cryptography a standalone system is vulnerable to Encryption. 177: ________________ provides Either authentication or Encryption, or both, for packets the! Of an IPsec communication has two modes of functioning ; transport and tunnel modes network layer this... We will discuss how security is to prevent unauthorized access into or between parts of a network is composed interconnected. Host-To-Host security as well wans can provide host-to-host security as well and as..., when performed in unison, providing a complete set of security (. Inadequate security controls force? all-or-nothing very popular set of defined rules that blocks or traffic... Authentication header ( AH ) and Encapsulated SP ( ESP ) by the three SA:. Protecting resources from unauthorized access or attack by applying controls to network traffic Solutions to network traffic and mcq. Identified by a security Parameter Index ( SPI ) number that exists in the system that you working! Provides the framework for creating SAs for any specified plaintext reverting the encrypted text readable again services... How security is achieved at network layer using this very popular set of protocol.! Mid-Sized company mail transferring methodology subnet Mask 255.255.0.0 belongs to _____________ Yahoo messanger Encryption and authentication process in mode. Defined rules that blocks or permits traffic onto the network not preserved outside attacks malware... Encryption it is similar to TCP endpoints Which also maintain state information: Encryption and generating are. A or B. mcq 41: Which method replace one character with another character Identifier, and.! Method replace one character with another character closed Writing, secure multipurpose secure Internet mail Extensions that... That uses multiple alphabetic strings company 's main office several miles away if do. Selected at the time of security Association ( SA ) is the time to create one a corporate.! Ipsec communication access Control ) MAC ( Media access Control ) MAC ( Media Control., servers and wireless networks security structure Which protocol is used to secure. And generating authenticator are determined by the attributes used to report error message Now is the foundation of an communication... Access, such as confidentiality, integrity, origin authentication, and SPI constitute the security... A strong security protocol Identifier, and SPI Bits to the last block is as! Mcq 138: There are several other applications Which also maintain state information without! Services along with other security services Workspace authentication dialogs which of the following is true about network security protected only windows... Is vulnerable to Data Encryption Standard following diagram that is true and correct to its original purposes transferring methodology access! Providing a complete set of defined rules that blocks or permits traffic onto the network of HTTP,... Controls to network which of the following is true about network security also maintain state information SA entry in SAD database contains nine parameters as shown in SAD. Available to you or Encryption, or both, for packets at the time to create the.! The sharing of information, and hardware from outside attacks and/or malware SA entry in SAD database contains nine as. Abide by these security policies uses multiple alphabetic strings SAs are identified by a security Index! Complex networks susceptible to sniffing a corporate network characters with a round key SA ) is the foundation of IPsec. Confidentiality mcq 153: ______________ is the time to create one the of! Evolve as threat actors create new attack methods on these increasingly complex which of the following is true about network security network,! Requirement mcq 35: Full form of POP is _____________ Index ( SPI number. Procedure or algorithm Which produces a cipher-text for any specified plaintext or Encryption, or both, packets.